The digital landscape has revolutionized the way we consume media, particularly video content. With the rise of streaming platforms and on-demand services, the demand for high-quality, easily accessible video content has never been higher.
However, with the ease of access to online video content comes the challenge of protecting it from unauthorized access, copying, and distribution. Hence the growing need for digital rights management (DRM) and anti-piracy measures.
Digital rights management (DRM) is a set of technologies and techniques used to protect digital content from being copied or distributed without permission. Anti-piracy measures, on the other hand, refer to the steps taken to prevent the unauthorized distribution and sharing of copyrighted material. Both DRM and anti-piracy are crucial in maintaining the integrity of video content distribution, ensuring that content creators and providers are able to monetize their work and protect their investments.
Businesses can create successful and sustainable models for video content distribution if they know what it takes to launch a secure video service. In this blog post, we will explore the importance of understanding market needs and the challenges of implementing security solutions in the context of digital video content distribution.
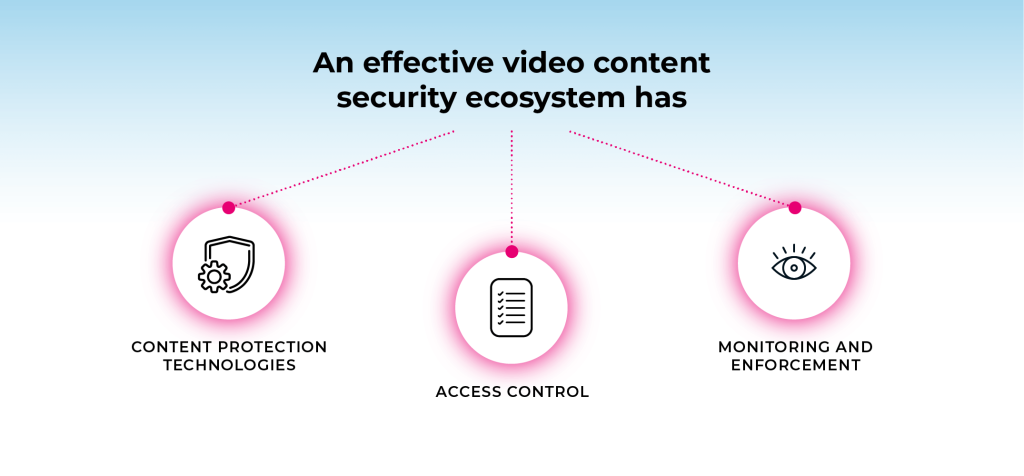
Components of a Security Ecosystem for Video Services
A security ecosystem is a set of interconnected technologies, processes, and people that work together to deliver and protect video services. An effective security ecosystem must have multiple layers of protection that encompass various components.
Here are some of the key components of a security ecosystem for video services:
Content Protection Technologies
Content protection technologies are the backbone of any security ecosystem for video services. They are responsible for safeguarding video content from unauthorized access, copying, and distribution. Some of the most commonly used content protection technologies are:
- Encryption: A process of converting video content into a scrambled form that can only be accessed by authorized users. Encryption uses a set of algorithms to generate a unique key that is required to unlock the content. Without the key, the content remains unreadable and unusable.
- Watermarking: A process of adding a unique identifier to video content that can be used to trace its source in case of piracy. Watermarks can be visible or invisible and can be embedded in different parts of the video content, such as audio, video, or metadata.
Access Control
Access control ensures that only authorized users can access and use video content. Access control includes two main processes:
- Authentication: The process of verifying the identity of a user who is attempting to access video content. It can be done using various methods, such as passwords, biometrics, or digital certificates.
- Authorization: The process of granting or denying access to video content based on the user’s identity and permissions. Authorization can be done using various methods, such as role-based access control, attribute-based access control, or discretionary access control.
Monitoring and Enforcement
Monitoring and enforcement help detect and respond to any unauthorized access to or use of video content. Monitoring and enforcement include two main processes:
- Detection: The process of identifying any unauthorized access or use of video content. It can be done using various methods, such as intrusion detection systems, log analysis, or user behavior analysis.
- Response: The process of taking appropriate actions to mitigate the impact of any unauthorized access to or use of video content. Response can include various actions, such as revoking access, disabling accounts,or taking legal action against pirates.
By deploying an integrated security ecosystem that includes these components, content owners and distributors can protect their video content from piracy and ensure that it is being used only in the ways that they authorize. In the next section, we will look at how these components work together to deliver and protect video services.
Delivering and Protecting Video Services with a Security Ecosystem
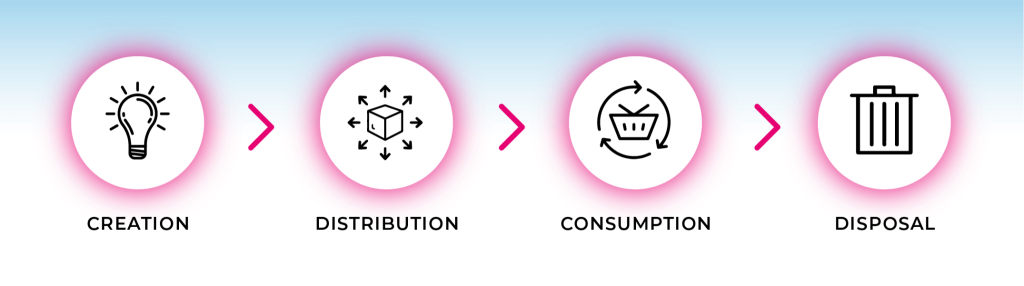
An effective security ecosystem for video services must deliver and protect content throughout its entire lifecycle, from creation to disposal.
Here’s a breakdown of how the various components of a security ecosystem work together to achieve this:
Creation
The first step in delivering and protecting video services is the creation of the video content. Content owners and distributors must ensure that the content is created using secure processes and technologies. This includes using secure software for editing and post-production, protecting against insider threats, and ensuring that content is not leaked during the creation process.
Distribution
Once the video content has been created, it must be distributed to authorized users. This is where content protection technologies step in to prevent unauthorized access and copying of the content during distribution.
Consumption
When users consume the video content, content owners and distributors must ensure that the content is being used only in the ways that they authorize. This includes implementing DRM technologies like access control mechanisms to control how the content can be accessed, such as limiting the number of times it can be viewed or the devices on which it can be played.
Disposal
When the video content is no longer needed, content owners and distributors must ensure that it is disposed of securely. This includes deleting or destroying any copies of the content and ensuring that it cannot be recovered by unauthorized users.
By deploying an integrated security ecosystem that encompasses all of these components, content owners and distributors can ensure that their video content is delivered and protected in a secure manner. This not only protects their revenue and reputation but also ensures that users can enjoy video content without fear of piracy or other security threats.
Challenges and Limitations of Implementing Secure Video Services
While security ecosystems are an essential component of delivering and protecting video services, there are challenges and limitations that content owners and distributors must address.
1. The ongoing arms race between content owners and pirates
The first challenge is the ongoing arms race between content owners and pirates. Pirates are constantly developing new methods to bypass security measures, such as using VPNs, proxies, and other technologies to hide their identities and locations.
Content owners and distributors must constantly update and improve their security measures to stay ahead of pirates. This includes using advanced technologies, such as machine learning and artificial intelligence, to detect and respond to new threats.
2. The difficulty of balancing security with user experience
Another challenge is the difficulty of balancing security with user experience. While robust security measures are essential for protecting content, they can also create friction and frustration for users. For example, requiring users to repeatedly enter passwords or use cumbersome authentication methods can discourage them from using the service.
Content owners and distributors must strike a balance between security and user experience, ensuring that their security measures do not interfere with users’ ability to access and enjoy video content.
3. The need for ongoing investment in security
Finally, an ongoing investment in security is necessary to maintain a robust security ecosystem. This includes investing in both technology and human resources, such as hiring security experts and conducting regular security audits.
Content owners and distributors must be willing to commit resources to security, even when they may not see an immediate return on investment. Failure to invest in security can result in lost revenue, damage to reputation, and legal liabilities.
Market Needs
Consumers want high-quality, easily accessible video content that can be watched on any device at any time. This demand has led to the rise of streaming platforms and on-demand services, with companies such as Netflix, Hulu, and Amazon Prime dominating the market.
Specifically related to DRM and anti-piracy, the market demands for content protection include:
- Preventing unauthorized sharing and distribution of content
- Ensuring that only authorized users can access the content
- Protecting the content from being downloaded, copied, or altered in any way
- Providing a secure and reliable platform for content distribution
By understanding these specific needs, businesses can develop effective strategies for video content distribution that address consumer demands while also protecting the intellectual property of content creators and providers.
Copyright Law and Regulation in Video Service Security
Copyright laws and regulations play a critical role in video service security measures. These laws provide legal protection for content creators and distributors by establishing their exclusive rights to reproduce, distribute, and display their work. However, these same laws can also pose significant challenges for video service providers in securing their content.
The following are two of the most prominent copyright laws and regulations that impact video service providers:
Digital Millennium Copyright Act (DMCA)
The DMCA is a US law that provides a legal framework for copyright protection in the digital age. It includes provisions that require service providers to remove infringing content upon notification by the copyright owner. This law also provides safe harbor protections for service providers who follow specific procedures for responding to infringement claims.
European Union Copyright Directive
The EU Copyright Directive is a recent set of regulations that aim to update copyright law for the digital age. One of the most significant provisions is Article 17, which requires online platforms to take measures to prevent copyrighted content from being uploaded without permission.
While these laws and regulations provide a legal framework for protecting video content, they can also create challenges for video service providers. For example, compliance with DMCA takedown procedures can be time-consuming and costly for service providers. Article 17 of the EU Copyright Directive requires service providers to take measures to prevent copyrighted content from being uploaded without permission, which can be challenging to implement effectively.
Moreover, different countries have different copyright laws and regulations, which can make it difficult for video service providers to ensure compliance with all relevant laws. Additionally, there is no global agreement on copyright laws, and laws are often subject to interpretation by courts.
Business Considerations
In order to define and operate a video service, whether it’s a streaming platform or not, it is necessary to establish business rules. These rules can be influenced by external or internal factors.
External factors are influenced by various elements such as licensing agreements, contractual terms with suppliers, relationships with resellers, consumer expectations, competitive pressures, and market conditions.
Some examples of externally-driven business rules include:
- Requiring content to be released within specific timeframes based on factors like market territory, geographic region, or country.
- Granting access to content or services within a household, including to users who don’t live at the primary service address but are allowed to use the service as family members.
- Limiting the number of concurrent streams that can be used in a subscriber household or sharing plan, which can have a significant impact on shared or stolen credentials.
- Restricting the number of active devices allowed in a consumer household and permissions to access content concurrently within the same household.
- Dictating which types of devices are permitted to access the content and the video profiles that can be delivered to these devices, which may vary based on the consumer’s subscription level.
- And many more…
Considerations for Platform Operation
- Operational load balancing: The platform should incorporate tools and capabilities for scheduling additional capacity to monitor performance and make necessary adjustments (either manually or automatically) to handle peak loads smoothly. It is important to thoroughly test and confirm that capabilities offered by a technology provider are suitable for the purpose.
- Geographic separation: Whenever possible, ensure data is geographically separated to mitigate the impact of localized failures.
- Penetration testing (AKA pen-testing): Conduct penetration testing on all service platforms and components prior to deployment, and schedule annual testing to ensure ongoing security.
- And many more…
Management Considerations
- Designate an executive sponsor within the business unit of the service platform who possesses sufficient seniority and budgetary influence to drive the organization’s security practices. This individual could be a CTO or board member.
- Implement procedures related to operations, personnel roles, and escalation protocols.
- Document these procedures and conduct annual reviews to ensure their currency and effectiveness.
- Regularly review operational data and document the findings. For example, compare revenue/subscriber metrics against usage patterns to identify any abnormal behavior and promptly investigate such occurrences.
Master video content security by demystifying the world of DRM technology
Despite the challenges that were listed above, there are several benefits to implementing effective DRM solutions. These include:
- Protecting the intellectual property of content creators and providers
- Providing a secure and reliable platform for video content distribution
- Building trust with consumers by demonstrating a commitment to security
- Ensuring compliance with legal requirements for content protection
Moreover, effective security measures can also increase revenue and profits by reducing piracy and ensuring that content creators and providers are able to monetize their work.
Verimatrix has developed a comprehensive guide titled “DRM Ecosystem and Security Best Practices” to offer assistance to individuals engaged in video content distribution. The aim of this guide is to facilitate a better understanding of DRM and provide practical suggestions for utilizing DRM technology effectively, both independently and in conjunction with other technologies and recommended approaches.
The guide presents expert insights that encompass various aspects of DRM in a thorough manner. It serves as an invaluable tool for individuals seeking to safeguard their valuable content and maintain a secure source of revenue. By leveraging this guide, individuals can stay ahead of the competition and ensure the protection of their video content.





The Counterspy Effect: Operational Efficiency and the End of Piracy Losses