Learn
Shift Left - CI/CD Integration
How XTD seamlessly integrates into a CI/CD pipeline.
Overview
In today’s fast-paced world, mobile app developers face increasing pressure to deliver high-quality apps quickly and efficiently. But with speed comes risk, and the risk of security breaches is higher than ever before.
That’s where Verimatrix comes in. We offer solutions that support shift left cybersecurity, which helps organizations improve their security posture, reduce the risk of security breaches, and deliver high-quality software more efficiently. This can be accomplished via CI/CD, a popular mobile software development methodology.
Shifting left and securing mobile apps with CI/CD.
As the world becomes increasingly reliant on software, security is a top concern for CISOs and SOC teams. To address this, many organizations are turning to the practice of shifting left, which involves moving testing, quality, and performance evaluation early in the development process. By doing so, teams can anticipate changes that arise during development that could impact performance or other delivery processes. This is where Shift Left Security comes in, providing comprehensive security throughout the entire software development lifecycle.
One way to implement shift left is through the use of CI/CD, or continuous integration and continuous delivery/continuous deployment.
What is CI/CD?
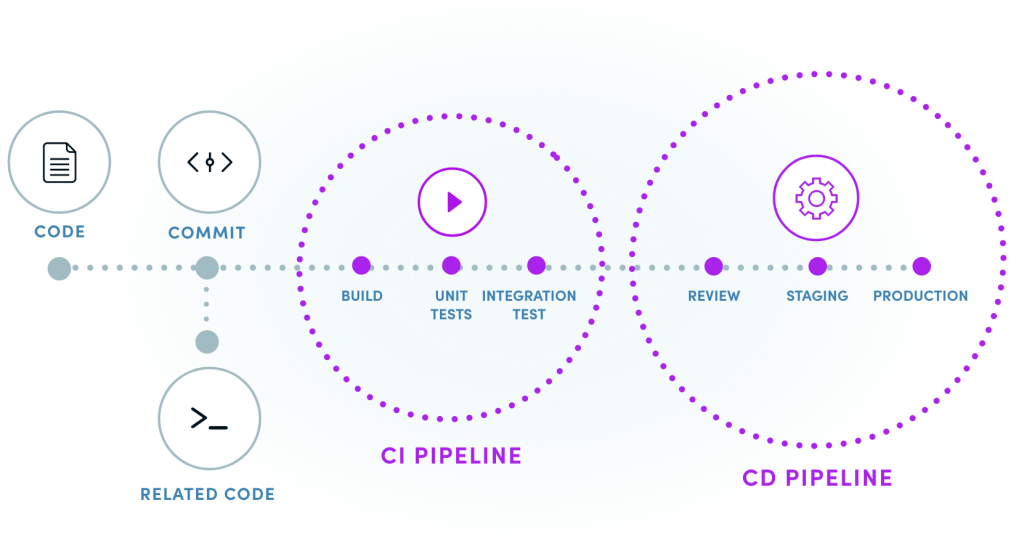
CI/CD Development Primer
1
First, we start by writing code for the app’s features and functionality. We make incremental code changes and store them in a version control system such as Git.
2
Use continuous integration (CI) tools to automatically build and test our code changes frequently and reliably. This helps us to detect any errors or bugs early on in the development process.
3
Once the code passes automated tests, continuous delivery/deployment (CD) tools are used to automatically deploy it to a staging environment. This helps test the app’s functionality and performance in a production-like environment.
4
If everything looks good in the staging environment, CD tools are used to deploy the code changes to the production environment. This is done in a fast and automated way, ensuring that the mobile app is always up-to-date and working as expected.
5
Throughout the entire CI/CD process, security testing and monitoring can also be integrated to detect and remediate potential security risks. This is known as sometimes known as shift left security, and it helps us to identify vulnerabilities and threats early on in the development process, reducing the risk of costly security breaches later on.
CI/CD’s popularity is on the rise.

CI/CD has become vital to many organization’s value streams. The book “Accelerate: The Science of Lean Software and DevOps: Building and Scaling High Performing Technology Organizations”, by Nicole Forsgren, PhD, Jez Humble, and Gene Kim wrote about CD being essential for achieving high organizational performance in software delivery. Using CD was shown to be a predictor of high organizational performance. You could say that the CD deployment pipeline is the value stream.

Assume breach and always verify
XTD collects data from devices and feeds it back so that it can detect anomalies in a compromised app or unmanaged device allowing a user to take a proactive approach by detecting breaches well in advance.1

Just in time access
Based on the risk posture of an organization’s Connected Apps and Unmanaged devices XTD can provide the information/signals to the back-end services (so that an administrator can allow or deny access or an ongoing transaction. XTD can also guide the backend services to provide restricted/limited/full access to corporate resources.2
Defense in depth
Based on the device security risk status, XTD advises financial/customer services to collect additional factors for authentication prior to network access or a financial transaction. Factors such as something you know, something you are and something you have.3
Popular CI/CD tools
There are several popular CI/CD tools that developers use to streamline their development process, improve code quality, and ensure smooth and reliable deployments.

GitLab CI/CD is a popular tool that helps developers automate their build, test, and deployment processes. It offers seamless integration with GitLab, a popular web-based Git repository manager.

Jenkins is an open-source automation server that is widely used for continuous integration and continuous delivery. It is highly customizable and supports a wide range of plugins and integrations.

Bamboo is a CI/CD tool from Atlassian that offers seamless integration with JIRA and other Atlassian tools. It supports multiple programming languages and frameworks and offers customizable workflows and deployment options.

Travis CI is a cloud-based CI/CD tool that automates builds and tests for GitHub projects. It is known for its ease of use and supports a wide range of programming languages and frameworks.

CircleCI is a cloud-based CI/CD tool that offers fast and reliable builds, tests, and deployments. It integrates with a wide range of tools and supports multiple programming languages and frameworks.
Cybersecurity can reduce risks.
With the increase in mobile app development comes an increase in potential cybersecurity risks. That’s why having security built into your CI/CD process is necessary in detecting and remediating potential risks. If your teams have not yet integrated cybersecurity into your CI/CD process, you should. But we realize you may face resistance to doing so.
Common barriers to cybersecurity implementation into CI/CD include:
• Resistance to change
• Lack of security expertise
• Time and resource constraints
• Lack of management support
• Compliance requirements
Overcoming these barriers requires a commitment to change and a willingness to invest in the necessary resources and expertise. But many do not. Here is what Gitlab included in their report, Mapping the DevSecOps Landscape, 2020 Survey Results:
Secure your app development supply chain.
Verimatrix offers state-of-the-art “shift left cybersecurity” — a comprehensive security solution that provides security across the full software development lifecycle. We safeguard your mobile app with layers of professional grade protection, and with our zero code, agentless app telemetry, we can help you monitor every connected device communicating with your app, detecting threats before they weaponize against you.
Secure your enterprise today.
Protect your mobile applications, your revenue, and your business with frictionless security.
We’re here to help
- Find the right solution for you
- Schedule a demo
- Explain our pricing
Trusted and Recognized
By industry analysts, associations, and peers



Trusted and Recognized
By industry analysts, associations, and peers


