From ransomware attacks to data breaches, cybercriminals are constantly seeking new ways to exploit vulnerabilities and steal sensitive information. Organizations of all sizes face a growing risk of experiencing significant downtime, financial loss, and reputational damage in the event of a cyber attack.
Organizations must therefore be aware that, if cyber attacks are inevitable, building cyber resilience is a necessary approach to countering them. Cyber resilience refers to the measures put in place to minimize and recover from cyber incidents as quickly as possible.
To drive for more cyber resilience protocols as standard procedure for all organizations, the European Union (EU) has taken a significant step forward with the “Cyber Resilience Act.” In the following sections of this blog post, we will examine this important legislation in more detail and explore its potential impact on technology development.
What is cyber resilience?
Cyber resilience is the ability of an organization to anticipate, withstand, respond to, and recover from cyber incidents and disruptions that may compromise critical business operations, assets, and information.
Cyber resilience measures include redundant systems and backups, incident response plans, employee training, and business continuity and disaster recovery plans. These measures enable businesses and organizations to quickly detect and respond to cyber incidents, minimize their impact, and recover from any damage.
Why do organizations need cyber resilience?
The list of cybersecurity solution types is extensive and includes firewalls, anti-virus software, intrusion detection, extended threat defense and response, application security, virtual private networks, and much more. Each solution has a distinct role to play in an organization’s overall security infrastructure.
Unfortunately, no matter how robust your cybersecurity measures are, there is no such thing as a completely foolproof system.
- The cost of cybercrime is predicted to hit $8 trillion in 2023 and grow to $10.5 trillion by 2025.
- A joint report by IBM and Ponemon Institute stated that it takes an average of 277 days for security teams to identify and contain a data breach.
- In 2022, the number of phishing attacks increased by 61% with the third quarter of the year experiencing a total of 3 million phishing attacks.
Cyber resilience is a crucial component of any organization’s risk management strategy. It allows businesses to continue operations in the face of cyber threats, ensuring that customers, employees, and partners are not adversely affected.
By planning for and responding to cyber incidents, businesses can reduce the impact of these incidents and minimize the costs of recovery.
Cybersecurity vs cyber resilience: Key differences
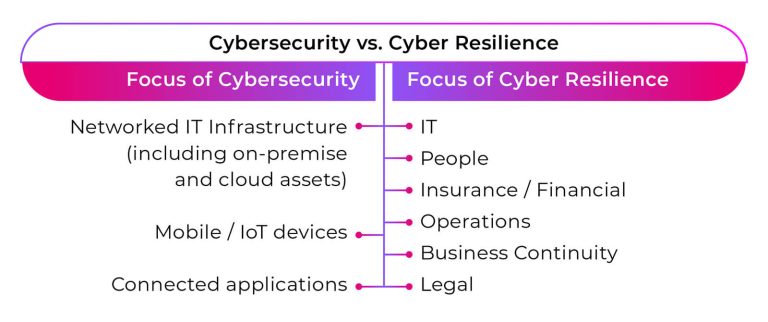
While cybersecurity and cyber resilience share the common goal of protecting against cyber threats, they differ in their approaches and objectives. Here are some key differences between the two concepts:
1. Focus
The primary focus of cybersecurity is to prevent cyberattacks by implementing measures such as firewalls, encryption, and access controls.
Cyber resilience, on the other hand, focuses on ensuring business continuity in the face of cyber incidents by implementing measures such as incident response plans, backups, and business continuity and disaster recovery plans.
2. Response
In cybersecurity, the response to a cyberattack typically involves identifying and mitigating the attack, restoring systems and data, and preventing further attacks.
In cyber resilience, the response to a cyber incident involves identifying and containing the incident, activating incident response plans, and implementing backup and recovery measures to ensure business continuity.
3. Timeframe
Cybersecurity measures typically operate in real-time, constantly monitoring systems and data for signs of cyber threats.
Cyber resilience measures, on the other hand, are focused on longer-term planning and preparation, ensuring that businesses are able to respond effectively to cyber incidents and recover from any damage.
A comprehensive cyber protection strategy should include a combination of cybersecurity and cyber resilience measures tailored to the specific needs and risks of each business or organization.
By implementing both cybersecurity and cyber resilience measures, businesses can ensure that they are adequately protected against cyber threats and that they are able to continue operations in the face of cyber incidents.
What is the EU Cyber Resilience Act?
The European Union Cyber Resilience Act (CRA) is a legislative initiative aimed at enhancing the resilience of EU member states against cyber threats. The CRA establishes minimum cybersecurity and cyber resilience standards for businesses and organizations operating in the EU.
A new term is introduced in the CRA called “products with digital elements” (PDE), which refers to any software, hardware, or device that either processes data or has the ability to connect to a network. This term also includes individual component parts of such products.
What does the EU Cyber Resilience Act require?
The EU Cyber Resilience Act’s main objective is to strengthen the regulations on cybersecurity to guarantee more secure hardware and software products, which are frequently targeted by successful cyberattacks.
According to the European Commission, there are two significant issues that impose additional costs on end-users and society:
- Hardware and software products have a low level of cybersecurity, which is demonstrated by prevalent vulnerabilities and inadequate and irregular provision of security updates to tackle them.
- End-users lack sufficient knowledge and access to information, which hinders their ability to choose products with adequate cybersecurity features or use them securely.
Key provisions of the EU Cyber Resilience Act
The EU Cyber Resilience Act sets out a number of key provisions that businesses and organizations must adhere to in order to enhance their cyber resilience. The CRA places a particular emphasis on critical infrastructure and essential services, which are deemed to be the most vital assets of the EU and its member states.
The CRA will be applicable to manufacturers, developers, and distributors of both hardware and software products that have connected digital components. The proposed legislation defines four specific objectives to ensure that:
- The products sold in the EU market are more secure by mandating a consistent cybersecurity framework that manufacturers and developers must adhere to.
- The manufacturers are accountable for addressing the cybersecurity of their products throughout the entire lifecycle, from the design phase to the product’s retirement.
- There is increased transparency regarding the security features of products, enabling businesses and consumers to make informed decisions about the cybersecurity of the products they purchase and use.
- There are clear guidelines regarding regulatory oversight and enforcement of the new rules and regulations.
The CRA does not apply to the following products, as they are managed under separate legislation:
- Medical devices
- Motor vehicles
- Military hardware
The manufacturers, developers, and distributors affected by this new law will face significant implications. Some of the proposed requirements stipulate that products should:
- be designed, developed, and produced with limited attack surfaces, ensuring an appropriate level of cybersecurity based on the risks.
- be delivered without any known exploitable vulnerabilities and with a secure by default configuration.
- protect against unauthorized access through appropriate control mechanisms.
Moreover, manufacturers will be obligated to:
- maintain the confidentiality of stored, transmitted, or otherwise processed data, and only process data necessary for a connected product’s intended use.
- identify and document vulnerabilities and components in products, resolve them promptly, and disclose them as soon as security updates become available.
- provide detailed information and user instructions regarding a specific product’s cybersecurity and how to install security-relevant updates.
How will the EU Cyber Resilience Act address non-compliance?
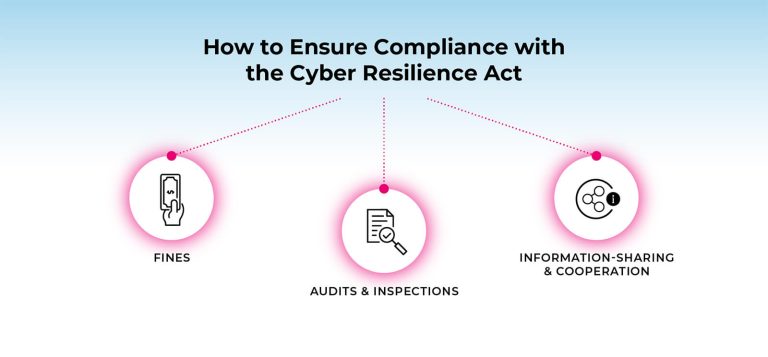
Within the EU Cyber Resilience Act, a system of penalties has been outlined for those businesses and organizations that fail to comply with its requirements. Depending on the severity of the breach, the fines for non-compliance could range from either (1) €5 million–€15 million or (2) 1%–2.5% of the organization’s global annual turnover, whichever is higher.
The CRA also divides violations into three categories:
- Breach of essential requirements;
- Breach of other CRA requirements; or
- Failure to provide accurate information to the authorities.
To ensure compliance with the CRA, national authorities are also required to carry out audits and inspections of businesses and organizations. These audits and inspections may be conducted either on a regular basis or in response to a specific security incident.
During an audit or inspection, the national authority may review the organization’s cybersecurity measures and safeguards, incident response and recovery plan, and other relevant documentation to ensure that the organization is in compliance with the CRA’s requirements.
To enhance the effectiveness of the CRA, it also includes cooperation provisions that encourage information-sharing and cross-border cooperation between national authorities and businesses and organizations.
These provisions are designed to facilitate the timely sharing of information about cyber threats and security incidents and to enable national authorities to work together to respond to and mitigate the impact of cyberattacks.
CRA certification requirements by product type
To address the risks of cyber threats and attacks, the Cyber Resilience Act sets out certification requirements for different types of digital products, services, and processes. These certification requirements are designed to ensure that digital products are secure, resilient, and can withstand cyber threats and attacks.
By certifying products and services according to the CRA framework, manufacturers and vendors can demonstrate that their products meet certain standards of cybersecurity and cyber resilience, which can help increase consumer trust and confidence in these products.
The CRA proposes three categories of PDEs based on their level of risk: Critical Class I, Critical Class II, and Default.
Default
The Default category includes products that do not have critical cybersecurity vulnerabilities, such as word processors, hard drives, video games, photo editors, and smart appliances. About 90% of products sold in the EU fall into this category.
Manufacturers of Default products are allowed to self-assess and self-certify their compliance with the CRA’s requirements, but they must complete technical documentation, submit a written declaration of conformity, affix a “conformity mark,” and regularly test for vulnerabilities.
Critical
Critical Class I and II products, such as mobile and desktop devices, IoT devices, and microprocessors, are considered higher-risk. Manufacturers of these products must undergo a compliance process with the regulatory body designated by each EU member state.
- Class I products have a higher level of risk than Default products, but a lower level of risk than Class II products. Class I requires the application of a standard form or third-party assessment to demonstrate compliance.
- Class II products have the highest level of risk and require a third-party assessment to demonstrate compliance with more stringent CRA obligations.
Each EU member state must designate its own market surveillance authority to ensure effective CRA implementation and manufacturer compliance, which may require cooperation with each other and ENISA for product concerns and CRA enforcement.
Understanding the EU Cyber Resilience Act: A deeper dive
To gain a deeper understanding of the CRA, Verimatrix has released a whitepaper titled “Security First: The European Union’s Cyber Resilience Act and Its Pending Impact on the Mobile App Development Ecosystem.”
This whitepaper provides more in-depth insights into the CRA’s key provisions and discusses the CRA’s potential impact on businesses and organizations operating within the EU.
If you’re someone seeking to understand the CRA and its implications for cybersecurity in the European Union, this whitepaper is an essential resource. You can download a free copy today!
How will the EU Cyber Resilience Act impact technology development
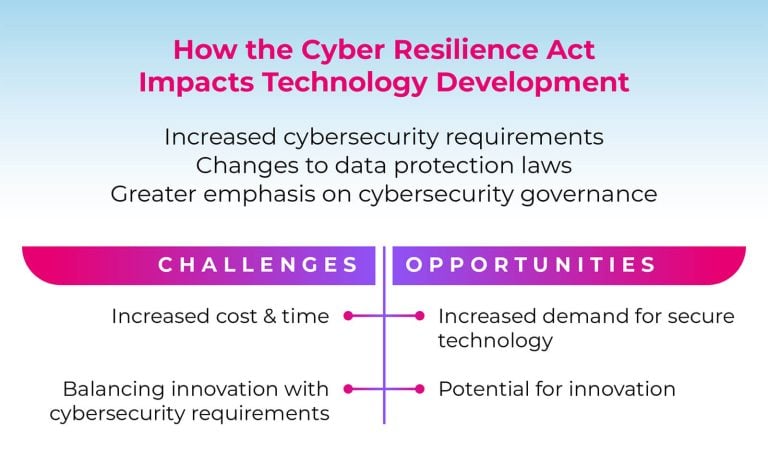
The EU Cyber Resilience Act will require developers and manufacturers of hardware and software products to evaluate and modify their practices to enhance the security of their products.
1. Increased cybersecurity requirements
One of the key ways that the CRA will impact technology development is by introducing mandatory cybersecurity requirements for certain critical infrastructure sectors. This means that technology companies that develop products and services for these sectors will need to ensure that their offerings meet the new cybersecurity standards.
The new cybersecurity requirements are likely to have a significant impact on software development. Developers will need to ensure that their software is secure and resistant to cyberattacks. This may involve incorporating security features, such as encryption and access controls, into the software’s design.
The new cybersecurity requirements may also impact hardware development. For example, hardware components used in critical infrastructure sectors may need to be designed with built-in security features, such as tamper-proofing and secure boot.
2. Changes to data protection laws
Another way that the CRA may impact technology development is by introducing changes to data protection laws. The act includes provisions that strengthen data protection requirements for critical infrastructure sectors.
This may have an impact on data-driven technologies, such as big data analytics, which are used in critical infrastructure sectors. Developers will need to ensure that their data-driven technologies comply with the new data protection requirements.
The new data protection requirements may also impact artificial intelligence and machine learning technologies. Developers will need to ensure that their algorithms and models are trained on data that complies with the new data protection requirements.
3. Greater emphasis on cybersecurity governance
The CRA places a greater emphasis on cybersecurity governance. This means that technology companies will need to have a more robust cybersecurity governance framework in place.
This may have an impact on technology company leadership. Senior executives and board members will need to take a more active role in cybersecurity governance, including setting cybersecurity policies and overseeing cybersecurity risk management.
The greater emphasis on cybersecurity governance may also impact the role of cybersecurity professionals. These professionals will need to ensure that they have the skills and expertise to operate within a robust cybersecurity governance framework.
Challenges for technology development
Increased cost and time to develop secure technology
Developers will need to invest in new security features and undergo certification processes to ensure that their products meet the new cybersecurity standards.
For smaller technology companies, this could be particularly challenging, as they may not have the financial resources or expertise required to meet the new cybersecurity requirements. This could result in a consolidation of the technology industry, with smaller companies being acquired by larger companies with more resources to invest in cybersecurity.
Difficulty in balancing innovation with cybersecurity requirements
Developers may be hesitant to incorporate new and innovative features into their products if they do not comply with the new cybersecurity standards. This could stifle innovation in critical infrastructure sectors, as companies may prioritize cybersecurity compliance over innovation.
Opportunities for technology development
Increased demand for secure technology
With the new cybersecurity requirements in place, there is likely to be a greater demand for technology products and services that meet these standards. This could create opportunities for technology companies that specialize in cybersecurity to develop and market new products and services that meet the new cybersecurity standards.
Potential for innovation in cybersecurity technologies
With the introduction of new cybersecurity standards, there is likely to be a greater demand for new and innovative cybersecurity solutions, such as artificial intelligence-powered threat detection systems or blockchain-based security protocols. These new cybersecurity technologies could help enhance the security and resilience of critical infrastructure systems.
5 steps to prepare for the EU Cyber Resilience Act
For those organizations that intend to keep the EU as part of their market, the following steps are generally helpful to prepare for the Cyber Resilience Act:
- Assess your current cybersecurity posture: Conduct a comprehensive assessment of your organization’s current cybersecurity posture, including the systems, processes, and personnel involved. This assessment will help you identify any gaps in your cybersecurity practices and determine which areas need improvement.
- Identify potential gaps in compliance with the CRA: Review the key provisions and requirements of the CRA and identify any areas where your organization may fall short. This could include data protection measures, incident reporting requirements, or other security-related provisions.
- Develop a roadmap for compliance: Based on your assessment and identification of gaps, create a plan that outlines the steps your organization needs to take to comply with the CRA. This roadmap should be specific, measurable, and achievable within a given timeframe.
- Implement necessary changes and improvements: Once you have a plan in place, it’s time to start implementing the necessary changes and improvements to your organization’s cybersecurity posture. This could include updating your security policies, deploying new security technologies, or providing additional training to your employees.
- Regularly review and update your cybersecurity measures: Cyber threats are constantly evolving, and your organization’s cybersecurity measures need to keep up. Regularly review and update your cybersecurity measures to ensure that they remain effective against emerging threats.
These are more specific steps that cybersecurity experts can take for their organization:
- Inventory audit: Conduct an inventory audit of your current applications and add in-app protection to all active ones. It’s recommended to only allow low-risk apps to connect to your cloud and server environments.
- Application security: Incorporate application security into your continuous integration/continuous development (CI/CD) processes.
- Detect & response: Deploy detect & response tools to monitor all connected devices, including unmanaged consumer endpoint devices that use your apps.
- Attack pattern detection & prediction: Introduce attack pattern detection and prediction capabilities to your SOC teams to mitigate future threats.
4 useful tips for achieving long-term cyber resilience
The EU Cyber Resilience Act is a positive step towards enhancing cyber protection in the EU, but businesses and organizations must go beyond the minimum standards set by the act to ensure that they are adequately protected against cyber threats.
- Adopt a risk-based approach: This involves identifying, assessing, and prioritizing potential threats to your organization’s systems and data. By focusing on the most significant risks, you can allocate resources effectively to minimize the likelihood of a successful cyberattack.
- Implement a cybersecurity framework: A cybersecurity framework provides a comprehensive, consistent, and structured approach to managing cybersecurity risks. Examples include the NIST Cybersecurity Framework or ISO 27001.
- Train employees on cybersecurity best practices: Employees are often the weakest link in an organization’s cybersecurity defenses. Over 70% of businesses cannot find staff with the required digital skills. Providing regular training and awareness programs can help ensure that employees are aware of the risks and know how to respond to potential threats.
- Have a response plan in place: Despite your best efforts, it’s possible that your organization may still suffer a cyberattack. Having a response plan in place can help minimize the damage and facilitate a quick recovery. Your response plan should include clear procedures for incident reporting, containment, investigation, and recovery.





