A cryptographic key transforms plain text into cipher text, then back into plain text. Cryptographic keys are random strings of random characters put in a particular order.
The purpose of cryptographic keys is to alter data to protect it from theft. You can call it encrypting, altering, transforming, or scrambling; all of these are accurate descriptors. The idea is that you turn plain text (normally code) into decipherable gibberish, at least in the eyes of anyone trying to steal or intercept it.
Without the key, a viewer can’t understand what they’re looking at. Naturally, this offers many cybersecurity benefits. Preventing fraud, intellectual property theft, and reverse engineering are among the most important benefits. That’s why cryptographic keys are ubiquitous parts of most people’s lives, whether or not they realize it.
Cryptographic keys can be produced and used in several ways. Let’s go over those types of cryptographic keys, the science behind them, and their applications and importance.
Types of cryptographic keys
Different types of cryptographic keys have different security requirements and, therefore, different use cases.
Symmetric keys: definition and usage
Symmetric keys enable symmetric encryption. That means that the keys for encryption and decryption are the same. You use one key to lock and unlock the same thing.
This is a very simple type of cryptographic encryption, but it’s sufficient in many scenarios. Symmetric keys are suitable when speed is of the essence and security risks are low. Data can be encrypted and decrypted faster and with fewer opportunities for confusion.
Two of the many use cases for symmetric keys include securing data at rest or quickly encrypting large volumes of data temporarily. However, relying on symmetric keys for too long may induce a false feeling of security.
Asymmetric keys: definition and usage
Asymmetric cryptographic keys are unmatching pairs: there’s a public key and a private key.
- The public key is distributed and used to encrypt data.
- The private key is a secret key that’s used to decrypt the encrypted data.
Certificate authorities (CAs) provide public/private key combinations using public key infrastructure. The registration process begins before the user’s certificate status is relayed to the CA.
Asymmetric keys provide a higher level of security than symmetric keys, so asymmetric keys are widely used for secure exchanges. Use cases include many things like digital signatures, secure communication, and SSL/TLS certificates for secure website communication.
Use-case-specific cryptographic keys
Hashing keys
Hashing keys are of a fixed size and are irreversible outputs derived from inputs of variable sizes. Hashing doesn’t require or involve encryption or decryption. These keys are used for functions like password hashing or authentication.
Digital signature keys
This is a specific use case for asymmetric keys. Digital signature keys are used to verify the integrity of data and communications.
One-Time Pad (OTP) keys
These are random, one-use-only cryptographic keys. They’re used for one-off instances, normally communications sessions. As these keys are self-destructive, they’re useful when repetition isn’t needed, especially in cases where privacy/secrecy are of the utmost importance.
The science behind cryptographic keys
Conceptually, cryptographic keys aren’t complex and are thus easy to grasp. But they’re made possible by complex underlying processes. The science behind them is what makes them such a powerful security tool.
Key generation algorithms
Key generation algorithms are mathematical processes that create secure cryptographic keys for encryption, decryption, or both.
Symmetric keys require algorithms to create secure, random numbers. It’s essentially a random number generator, providing one number for both encryption and decryption. You can think of it as a roll of the dice, except the dice have effectively limitless surfaces—and there are many dice.
With asymmetric key generation, a pair of keys is generated. One is private, and the other is public. The private key is kept secret and is only used to decrypt data that was encrypted with the public key. In these cases, the public key can be shared without risk.
Randomness and entropy in key generation
The key generation described above follows the importance of randomness in cryptography theory. To keep the key generation truly random, generators rely on sources of entropy. These are either:
- Random Number Generators (RNGs)
- Pseudo-Random Number Generators (PRNGs)
Hardware-based entropy can come in the form of replicating physical sources such as mouse movements or other electric signals. Software-based entropy comes from random data collected from OS data, like network packets or keystrokes.
In general, the more entropy that goes into key generation, the more secure the keys will be.
Of the two, PRNGs are less truly random. (Thus the “pseudo” before the RNG.) Computers are deterministic machines and therefore cannot be truly random. Instead, PRNGs are initialized with an entropy source, but they aren’t entirely randomized because they’re determined by an initial seed, and their keys are therefore relegated to a smaller selection.
Key length and its impact on security
The length of a cryptographic key is measured in bits. In general, the longer the key (the more bits), the more secure the key is from attack.
The key length affects:
- The durability of the encryption against attacks
- The feasibility of brute-force attacks
The latter is significant as brute-force attacks are quite common. It’s often possible to use random generators to attempt brute-force attacks. Longer keys make this less feasible as an attack method.
Key management & storage best practices
Following these best practices with cryptographic keys reduces the chance of successful attacks:
- Centralizing key management for better control and security
- Using random hardware number generators
- Avoiding weak algorithms
- Using secure storage (tamper-resistant HSMs, dedicated cold storage hardware devices, etc.)
- Implementing role-based access
- Retiring and rotating cryptographic keys regularly to reduce the plausible attack surface
- Adding multi-factor authentication (MFA)
- Monitoring and auditing regularly
Common cryptographic algorithms and key exchange
The most commonly used cryptographic algorithms are trustworthy and effective. You can use them as benchmarks for good practices in key generation algorithms.
Popular symmetric encryption algorithms
Some popular examples of past and present symmetric encryption algorithms are:
- Advanced Encryption Standard (AES)
- Data Encryption Standard (DES)
- International Data Encryption Algorithm (IDEA)
- Blowfish & TwoFish
- RC6
AES is the most popular symmetric encryption algorithm used today. It was developed as a replacement for DES, which was cracked back in 2005. AES has stood up to the test of time thus far. Compared to DES, it offers much longer encryption keys, so it rarely fails against brute-force attacks.
Blowfish and its more modern version, TwoFish, are also successors to DES. They’re both block ciphers like AES, but with longer key lengths (32 bits to 448 bits for Blowfish and 128 bits to 256 bits for TwoFish).
Popular asymmetric encryption algorithms
The most common past and present asymmetric encryption algorithms are:
- Rivest-Shamir-Adleman (RSA)
- Diffie-Hellman
- Elliptic Curve Cryptography (ECC)
RSA is the oldest of these algorithms, developed in 1977. It uses factorization of the product of two prime numbers to deliver encryption ranging from 1024 bits to 2048 bits. It’s a powerful method, with its main drawback being the demands of that power. That is, it offers one of the slowest decryption processes, but that slowness comes with an incomparable level of security.
An ECC curve can potentially reach an even more powerful level of encryption, up to 15,360 bits. It’s more widely considered to be the future of encryption.
The importance of key security: Best practices for cryptographic key usage

Key security is crucial if you want your cryptographic keys to serve the purpose they were designed for. To ensure this security, you must understand a few factors.
We’ve touched on most of the best practices for specific circumstances. To reiterate, these are the best practices that must be observed with all cryptographic key usage to guarantee the maximum level of safety.
Protecting cryptographic keys from unauthorized access
Avoiding unauthorized access is simply about keeping your keys secret. Unauthorized access can lead to all the encrypted data being compromised. Several malicious actions are possible at that point.
Robust security can be offered through:
- Hardware security modules
- Strong permissions systems
- Quality training and constant vigilance
Secure key distribution and transmission
The distribution and transmission of keys is an area of vulnerability. So, it’s crucial to establish secure connections between the relevant parties. During the exchange, interception is possible, leaving the encrypted data at risk.
Secure exchange protocols like Deffie-Hellman key exchange are a crucial step in ensuring security. In addition, only use secure channels (TLS) to defend against attempted Man-In-The-Middle (MITM) attacks.
With these steps, you have the strongest chance of ensuring only authorized parties receive the correct keys.
Key revocation and rotation strategies
Even with the best practices observed, you stand a chance of attack or even accidental exposure.
Key revocation and rotation backup plans must be in place to handle these threats, which may arise at a moment’s notice.
Regularly rotating keys and revoking compromised keys limits the possible attack surface. In other words, this presents a smaller window of opportunity in which attackers could take advantage of vulnerabilities. Key rotation is thus one of the few ongoing measures that can protect data and communications over time.
Using different keys for different purposes
Compartmentalization is the word of the day here. Think of it as a key management measure meant to diversify your security and handle areas of higher risk more appropriately.
Use different keys for:
- Isolating specific purposes
- Reducing the impact of one key becoming compromised
- Compartmentalizing accesses
- Adding flexibility to key rotation
Employing secure key storage mechanisms
In addition to rotating and replacing keys, you need to place them in secure storage. You have several options to this end:
- Trusted platforms
- Hardware security modules
- Smart cards
- Key vaults (e.g., Azure Key Vault)
- Secure cloud management services
- Physical, offline devices
- Secure data centers
- More
Implementing multi-factor authentication
Multi-factor authentication (MFA) provides an additional layer of security for your systems and user accounts. It requires more forms of authentication before access to any sensitive areas is granted.
MFA has a synergistic, complementary relationship with cryptographic keys. Using them wisely and in combination maximizes security against brute force and other attacks.
Real-world applications of cryptographic keys
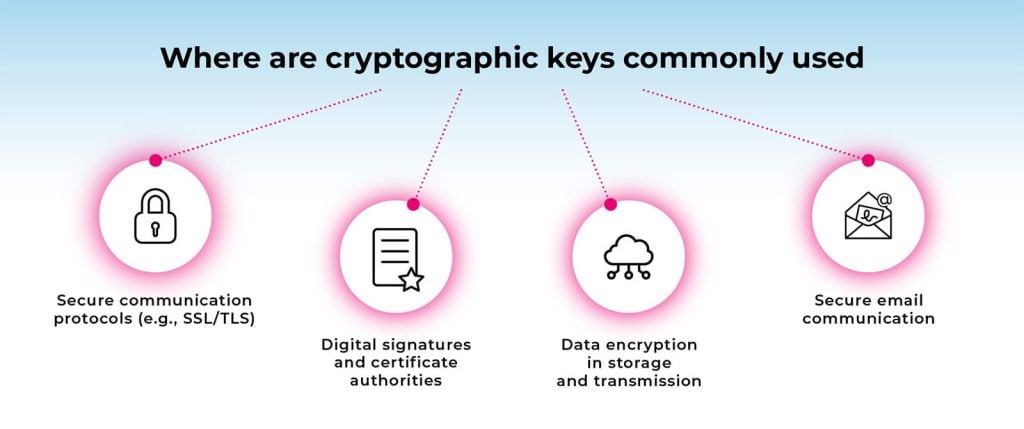
Cryptographic keys are a common part of many day-to-day functionalities.
Secure communication protocols (e.g., SSL/TLS)
Cryptographic keys are crucial to creating secure channels of communication over the internet. Public and private keys are applied together for asymmetric encryption during the SSL/TLS handshake process.
Digital signatures and certificate authorities
Digital signatures rely on cryptographic key exchanges to verify authenticity. They’re applied when digitally signing documents or verifying the authenticity of communications. Normally, the sender provides a private key to generate a unique digital signature. The corresponding public key can verify it.
Data encryption in storage and transmission
Both symmetric and asymmetric cryptographic keys are used for securing data at rest and/or during transmission. Either choice may work for these purposes.
Secure email communication
Cryptographic keys can be used to enable end-to-end encryption for email and other types of communication. Asymmetric private and public keys are used to encrypt and then decrypt the message.
These measures ensure that only the intended recipient can read the content of the message. Eavesdropping and interception are rendered much more challenging.
The bottom line
Cryptographic keys are a big part of cybersecurity. Applications people use normally take advantage of them in a way that most users can’t see or understand. Nevertheless, those who offer applications to end users must understand the best practices to ensure that information is only accessed by intended recipients.
Cryptographic keys are a crucial part of data security. They prevent interception, MITM attacks, and brute-force attacks.
To enhance your security, audit your own cryptographic key processes. Test their security with penetration testing and look into ways to further secure your communication. No matter how secure your data is, you should always strive to make it safer from cyberattacks.