Mobile application repackaging (sometimes called a cloning attack) affects developers of all sizes – from start-ups to enterprise companies. No matter how big your operation is or how many users download your app, it’s important for all developers and publishers to be aware of this attack vector. Application repackaging provides attackers an easy route to use your own intellectual property against you and your customers. Historically, repackaging attacks have been the most common vehicle for deploying malware to smart devices.
What is a repackaging attack?
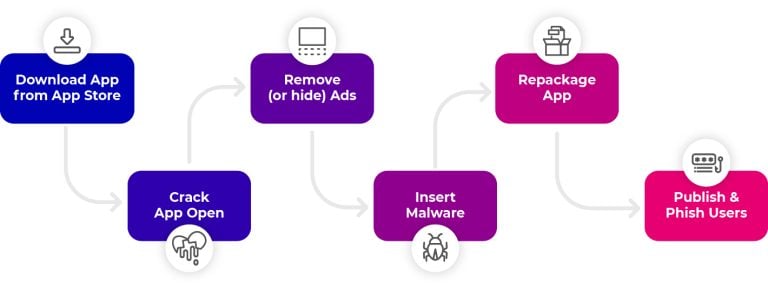
When an attacker is repackaging an app for their own purposes, they usually use these 5 steps:
- Take the original app from the app store (e.g. Google Play). This can be done using little more than a web browser.
- Crack open the app – open source tools are freely available and make it very easy for an attacker to do this.
- Modify the app – an attacker will make changes to your app to suit their purpose.
- Repackage the app using standard development tools.
- Convince users to download the repackaged app – criminals are extremely skilled at phishing and other tricks to get users to download malicious, illegitimate apps.
An attack of this nature is very effective because it is based on the developer’s original IP. This means that from the user’s perspective, the repackaged app behaves just as they would expect. The UX looks and feels the same and can trick even savvy users, leaving them oblivious to the fact they’ve actually installed malware. Repackaging attacks are also easy to perform – there’s no dark web magic required. The tools and knowledge are all freely available. Cyber criminals are attracted to this form of attack because it offers a huge return on a minuscule investment. Without naming names, let’s look at a few examples of how app repackaging has been used for malicious intent:
Repackaging an over the top (OTT) video app
Video streaming apps are a frequent target for repackaging. The nature of these offers good phishing material for cybercriminals – maximizing the attacker’s return on investment. For example, if the service is ad-funded, users will likely be interested in an “ad free” version of the app. In fact, in many cases, users will actively seek out an “ad free” version. To attract willing victims, attackers modify the legitimate OTT app by removing the advertisements. After stripping the apps of ads (and thus, your monetization efforts), they will also make other hidden modifications to the app, such as embedding spyware that siphons off user credentials.
It’s these hidden modifications that give the attacker their reward. Repackaged media applications deprive service operators of their advertising revenue. However, perhaps even more damaging is when the attack is exposed, and an operator’s app and brand become associated with a breach of personal data. As soon as your business name is in headlines for a security breach, reputation and value plummet along with revenue.
Intellectual property (IP) theft
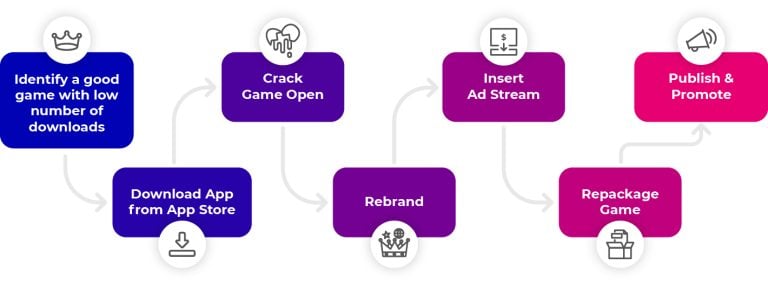
App stores are filled with engaging, entertaining games that never quite got the popularity they deserve. To add insult to injury, these games are perfect targets for attackers. Criminals will take a little-known game, change its branding, add advertising that pays the attacker, then republish it to app stores as if they’d developed it themselves. For less than a day’s effort, criminals can acquire a reasonably profitable revenue stream (usually making them more money than the original developer ever made).
How to prevent repackaging attacks
All applications installed on Android or iOS devices must be signed by the developer—it is not possible to install an unsigned app. For developers, the first line of defense is to simply prevent an attacker from resigning the app using the standard developer tools. If an attacker is able to resign the app, they can present it as their own. The second line of defense is to stop code modifications using Anti-Tamper technology. This prevents an attacker from modifying the executable code and keeps them from making changes to your app or inserting additional code.
Verimatrix Shielding solutions provide a strong defense against repackaging attacks. An Android or iOS app protected with these easily implemented solutions can validate that the signing certificate is from the original developer. A strong anti-tamper network is interweaved with functional code, which constantly validated that the code has not been modified while it executes.