Runtime Application Self-Protection (RASP) security is the most powerful approach to application security. It’s a strategy designed to add additional security during an app’s runtime. It ultimately enables live monitoring and protection as an application runs. This makes threat detection faster and more thorough than it would otherwise be.
So, why not jump right in and inject RASP security into your cybersecurity apparatus
Ultimately, RASP security is a powerful tool that has gained a lot of traction in the cybersecurity industry. But implementing RASP security has different implications for every business. Specific adoption rates can vary quite widely.
In this article, we will go over the many benefits of RASP security and why it’s so important right now. If you want to know more about the power of real-time protection against fast-evolving threats, read on.
How RASP works
RASP security works by directly embedding security controls into an application’s runtime environment. This enables the active monitoring of app behavior, the detection of anomalies, and real-time responses to any potential threats.
This is made possible by several core aspects of RASP.
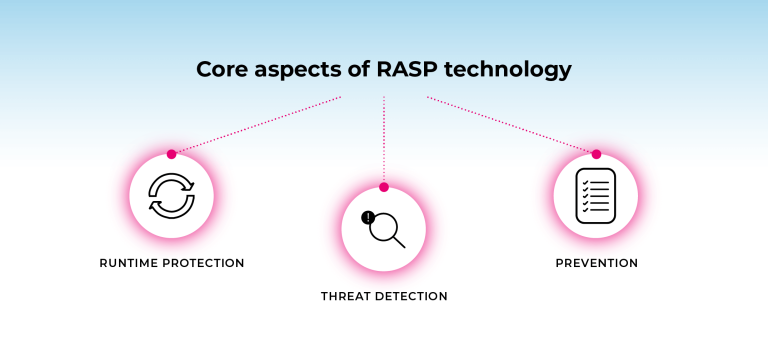
Runtime protection
Most other cybersecurity measures, especially the most traditional ones, rely on external infrastructure. RASP security is different in that it is injected into the runtime environment and, from there, acts as an agent. Think of it as your personal ‘Agent Smith’ protecting the matrix that is your application’s runtime environment.
Threat detection
RASP security takes a multi-faceted approach to threat detection, with preventative measures playing a part.
A normal RASP security apparatus includes several security mechanisms. Behavior analysis may play one part, while other common mechanisms include rule-based threat detection, machine learning, and AI.
RASP is a good option for some threats that other approaches are lackluster at fighting. It’s particularly good at detecting things like SQL injection attacks, code injection, and attempts to access applications without authorization.
Prevention
Another crucial aspect of RASP security is its highly proactive way of preventing threats from fully materializing.
This is one of many areas where RASP security is particularly proactive. RASP security systems can patch vulnerabilities detected in code. It can intuitively block inputs it believes to have been made with malicious intent. It can block suspicious activities that are underway in the runtime environment.
All of these measures add to the security benefits even before an attack has been successfully attempted.
Key benefits of RASP security
We’ve gone over how RASP security works in detail. But in practice, it provides organizations with more benefits than are initially apparent.
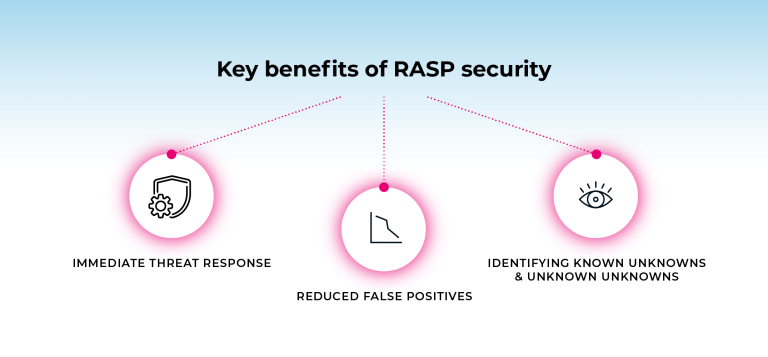
Immediate threat response
The nature of RASP security makes it the first gatekeeper in many situations. Embedded into applications’ runtime environments, it’s the immediate answer to an endless list of potential security threats that would otherwise succeed.
Real-time monitoring means constantly learning and detecting problems earlier than otherwise possible. Long-term, you get the fastest and most dynamic responses.
Reduced false positives
RASP security reduces false positives through greater runtime analysis, context-sorting, behavioral analysis, and machine learning. False positives are still possible, but the potential for their occurrence is greatly reduced.
Identifying known unknowns & unknown unknowns
It’s easy to deal with threats that you know everything about. But when new, strange threats emerge, the equation changes.
Unknown unknowns are the place where much attention needs to be paid today. New, emerging, or simply not yet identifiable threats require something beyond traditional cybersecurity approaches. RASP security fills the need here with machine learning-enabled behavioral anomaly detection, zero-day protection, and a broad focus on proactive approaches to runtime environment security.
How to implement RASP security
If you’ve decided to implement RASP security, you’ve already made a good decision. However, there are a few steps to take to ensure it’s implemented in a way that is as effective as possible for your business’s security.
1. Do an internal assessment
There are a number of RASP solutions on the market. Some of them will be a better fit for your application than others.
When assessing your business for cybersecurity while shopping for RASP security, consider your application’s:
- Programming language
- Deployable environment
- Framework
- Other niche considerations
Based on the above, some RASP security solutions will be ideal for you. Of course, you should also consider the overall trustworthiness and reputation of the provider.
2. Choose a solution
After considering your needs, choose the solution that is best. Take some time, as your choice will have ongoing implications.
3. Install and configure your RASP solution
Installing a RASP agent in your application’s runtime environment is the next step you will be directed to take. The actual agent will come in the form of some kind of module or as a library specific to your application’s language and framework.
Apart from understanding how RASP solutions work, this step is normally very easy to implement. The RASP solution will come with installation and configuration instructions to follow.
4. Customization
Once the RASP agent is installed and configured, you can choose the protection features you want to activate. You will normally be offered customization options for things like input validation, cryptography, and more.
You can enable and customize the features that fit best with your cybersecurity needs. It is normally recommended that you don’t just haphazardly activate all possible features. That may lead to worse performance or some functionality conflicts.
5. Testing, observing, & optimizing
You will want to watch the results of your RASP agent becoming activated very closely. There are a few reasons for this, the first of which is that some potentially negative things may result.
First and foremost, make sure that the addition of the RASP agent is not introducing new issues. For example, if your application suddenly becomes slower, you will know it’s likely the result of the change.
6. Update & assess
Make sure your RASP security is up to date. Install the patches as the vendor releases them. Those patches normally account for changes to the security landscape and any existing bugs.
As you update your RASP security, assess any noticeable changes that result. Look for the usual performance and functionality changes.
Limitations and challenges of RASP security
RASP security does have a few potential drawbacks. However, the benefits should outweigh the negatives, but only when certain conditions are met. You need to be aware of these limitations to help ensure that you meet those conditions.
Performance issues
This is one of the more common and severe challenges. RASP security places more demands on processing. The agent is integrated into the application, so it will slow everything down to some extent, whether that is an irrelevant or significant performance difference.
The impact on performance will depend on the complexity of the implemented security features. This is why we warned you to choose features carefully in the implementation guide above. So pay attention to how each feature affects the application’s performance.
Limited coverage
RASP security only offers additional protection during runtime. It will not offer any security benefits relevant to other security layers, including OS and network security.
Compatibility difficulties
RASP solutions are highly-tailored products. They are built for specific programming languages, environments, and frameworks.
Compatibility issues normally arise if the application in question uses unsupported technologies. Customers must ensure that their chosen RASP solutions support their stacks.
Ongoing maintenance
This is more of an inconvenience than a big challenge in most cases.
You will have to maintain your RASP security while monitoring the differences that updates make. This ongoing responsibility should be considered even before choosing a particular solution to implement.
RASP security comes with serious skill requirements. If you don’t already have them, you may need to hire the talent necessary to configure and manage your solution. If there is no existing talent in your organization, you will, at the very least, need to contract specialists to ensure everything works as intended.
Case studies: Successful RASP security implementation
Fortunately, if you’re wondering about the efficacy of RASP security, there are many examples to look at. Looking at successful examples of applications similar to yours may paint a better picture of the implications of RASP on app security and user trust.
Imperva AARP AWS protection
AARP approached cybersecurity firm Imperva with a request for help securing their Amazon Web Services-hosted applications from malicious activity. After an evaluation and integration with Imperva’s RASP agent, a long-term arrangement was agreed upon, which included ongoing protection and permanent patching.
After the application had the RASP agent integrated, they reported:
- All applications have been deployed faster
- Immediate impact on vulnerability management SLAs
- Downgrading of vulnerabilities across the board
Ultimately, AARP had a long backlog of vulnerabilities prior to RASP security implementation. It immediately became less critical, and more time was freed for their dev teams to focus on problem-solving solutions.
Verimatrix banking app protection
Jia-Xin, a creator of banking mobile apps, faced the threats we’ve discussed firsthand. She protected the world’s #1 banking app, among others. All her banking apps were popular targets for hackers, a problem that she approached Verimatrix to fix.
The main problem here was the frequency of application attacks. Given the obvious potential gains of a successful breach of a web banking app, many problems arose. Banks can afford to lose some money, but they cannot afford the PR nightmare and customer panic resulting from a successful breach. The security needs were difficult (not to mention costly) almost from the start.
Verimatrix Code Protection was the solution, injecting self-defending security into her web banking apps. Implementation was seamless and easy.
The results:
- All banking apps received proactive, enhanced protection from frequent and increasingly sophisticated attacks in real time.
- Ongoing obfuscation, environmental checks, jailbreaks, and root detection
- No code changes or SDK integration required
Future trends in RASP security
The cybersecurity industry is one of the most dynamic in the world. It changes quickly, and RASP security is also seeing its own changes. Most trends reflect the continuous development of enhanced technology that better protects applications.
1. There is a growing need for better mobile app security.
Organizations are continuing to shift toward Internet applications as a core part of their business. Cybercriminals are very well aware of this, and data breaches in particular are on the rise.

According to Verizon, web application breaches accounted for 43% of all breaches in 2020. The total number of data breaches via web application incidents has doubled since 2019.
Since then, cybercrime has skyrocketed across the board. Applications are still one of the primary targets. NowSecure reported in 2022 that over one in four mobile applications had at least one high-risk security vulnerability.
Going forward, the need to address application vulnerabilities isn’t likely to stagnate or decrease. If you’re managing one of those 1 in 4 applications with high-risk vulnerabilities, the time to worry was years ago. Now is the time to be hyper-vigilant, which is exactly what RASP security offers.
2. Artificial intelligence (AI) will see more use in cybersecurity solutions.
Artificial intelligence has become the name of the game in 2023. For RASP security, that means AI-based threat detection.
AI-based threat detection has the potential to produce several extremely positive results:
- Better threat detection accuracy
- A better understanding of threats through machine learning
- More dynamic behavioral analysis
- Reduced errors
- Earlier detection of zero-day attack attempts
- Better adaptability to the most recent cybersecurity threats to application’s runtime environments
3. Cloud-native RASP solutions are seeing greater demand.
Cloud-native solutions are tailored to the security needs of cloud-native environments. They are a necessary adaptation to trends in application deployment.
RASP solutions like these address challenges such as:
- Container-level protection
- Service mesh integration
- API security
4. Integration with DevSecOps practices is highly recommended.
RASP security measures must be agile and continuous. Several needs drive RASP integration with DevSecOps.
First, real-time protection is enhanced when RASP is integrated with DevSecOps. Integration helps ensure a minimal window of time between detection and damage. It’s also important to note its benefits for monitoring, response time, collaboration, and dynamism.
The bottom line
RASP security is a much-needed solution in a world where your online applications are some of the juiciest targets for cybercriminals. Runtime environment security implies certain needs, for which the implementation of RASP is the ideal solution.
If you truly want to minimize the threats, consider implementing RASP soon. It’s an essential layer of defense in an area that is constantly evolving. Dynamic threats require dynamic security, and your apps are safer with the added protection it provides.