A long-known major threat to mobile apps has made its presence known in a big way in the last few months, becoming more dangerous with new logistics of attack. Looks can definitely be deceiving—and that’s especially true with these types of threats. Cybercriminals have expanded what was once largely limited to well-known overlay attacks on web applications to users’ mobile devices today, and more specifically, their highly trusted mobile apps.
New criminal “services” have lowered the entry threshold for attacks significantly. These fast-growing overlay attacks mark a renewed need for user vigilance and greater app developer security precautions.
This threat advisory explains what you need to know and look out for in order to steer clear of these types of threats. Mobile app developers, especially, need to take heed, as these threats take advantage of the innate confidence that big brands enjoy when users rely on their associated mobile apps. And CISOs, now that mobile apps connect to your critical infrastructure, you need to better understand how this weak link in your security defenses could easily take you down—and how you can prevent this.
When an overlay attack tricks users into putting their data into what looks like their legit banking or media application, the malicious work begins in earnest—literally covering up part of the legit app with attacker-controlled screens that can capture logins, passwords, one-time codes, complete credit card data, banking transactions, and credit card transactions—all of it can be gathered by the cybercriminals and accounts can be abused or resold.
Here’s what’s happening given this new threat type.
First off, these threats mainly affect Android devices. A typical way for the attacker to enter the targeted user’s device is to bait the Android user into downloading an app that has a malicious payload (usually a free game, a video editing app, a flashlight app, etc.). This is a malicious app.
There are other ways to inject malicious code, like zero-day attacks that exploit, e.g., the latest z-day vulnerabilities on some Nexus and Samsung devices, to allow an attacker to enter a mobile device just by knowing the target’s phone number.
In response, companies are spending big to preventively protect their apps, just as they’ve done so with authentication in recent years. However, tons of apps obviously remain unprotected, and users still don’t have visibility into what’s potentially happening on their devices.
Unfortunately, most apps simply aren’t protected, and for some of the attacks, there is no protection available on the platform, so the best defense is for users to look out for the actual malicious overlay technique while they’re using their apps. It’s difficult to spot because the fake app acts like the legit one—and that’s exactly what cybercriminals bank on happening in their favor. Once that goes unnoticed, there’s nothing to immediately alarm the affected end user that their private information is likely on its way out the door.
How it works.
This malicious app has a “dark side.” Let’s use a banking app as an example. If the device does not have the targeted legitimate banking app installed and launched, the malicious app won’t do anything malicious. However, if the user has the targeted app on their phone, this malicious app will run in the background, waiting for that targeted app to be launched by the victim.
As soon as the victim launches the targeted banking app, the malicious app detects it and quickly takes over the screen. Typically, it will display a screen that is identical to the app’s login screen on top of the app’s login screen—and to the victim, it looks identical to the normal operation they’re used to experiencing.
The targeted app is launched, and the login screen is shown. The victim has nearly no way to know that the malicious app is overlaying their banking app’s input screen and is listening to all the user’s inputs. Variants of this attack take over the input screen and also ask later down the flow to renew or add credit card data after login, or they add similar fake requests that trick the user into exposing private data.
The victim enters their valid credentials or other secrets, which are collected by the malicious app that sends them to a so-called Command and Control server. If OTP authentication is required (the text message you get that provides a required temporary number), then the malicious app grabs that number and sends it to the Command and Control server. At that point, the Command and Control server has all the information needed to take over the victim’s bank account.
Depending on the attacker’s strategy and target of theft, the malicious app will either just let the users continue with their app (and abuse, for example, the stolen credit card data) or force the targeted user to restart the process by crashing the legit app and not take over the login screen in the next attempt.
Banks often send messages to alert users of activity on their accounts. Depending on the level of control the malicious app has obtained, in order to make sure the user does not receive these messages, some variants of the malicious app can take over the phone and disable all user interfaces. The victim cannot access any app, cannot receive calls, cannot place calls, etc. The victim cannot even reset or restart the device. With some variants of these attacks, the phone is only released from the malicious app’s grip after the battery is drained, recharged, and rebooted.
What is overlay web inject attack?
Overlay web inject attacks are a type of cyberattack that targets mobile apps.
Attackers inject malicious code into legitimate apps to create fake overlays that look like part of the app.
These fake overlays are designed to steal sensitive information, like login credentials or credit card numbers, entered by users.
Low cost of entry for bad actors.
These overlay attacks (also known as “UI redress attacks”) are now common offerings. A few months ago, a new dark web store began to surface, allowing attackers to conduct this attack via many different attack plugins for only $30.00. These plugins work with a set of widely used attack frameworks, like Hydra, Alien, or Cerberus. Lowering the entry threshold to that low price is a game changer. It’s making the attack much more dangerous.
Indeed, the low $30.00 plugin price isn’t a criminal’s only related “investment,” but it’s clearly a driver for its growth. That plugin that’s targeting a specific app needs to be placed into a framework that helps provide the malicious app with ways to trick the victim into installing the app and the Command and Control server. These attack frameworks cost between $1,000-$2,000 and can be reused many times.
Malware abilities
Add any permission to itself, including reading and sending SMS, reading files and so on.
Steal MFA messages from SMS and email and hide them from the user.
Full remote access control and screen recording. The malware stops the user from uninstalling it.
Steal information displayed in all apps and change the user input.
Post-exploitation the malware locks the phone and stops the user from calling, messaging or doing anything.
Variants of the threat and a specific look at inthebox web injects.
Already making headlines worldwide, some of the more notable variants of these types of attacks include:
With a specific look at InTheBox, it takes abuse of web injection and utilization of existing frameworks such as Alien, Ermac, Octopus, MetaDroid, Cerberus, and Hydra to a whole new level. InTheBox achieves this by offering more than 1,900 of those plugins described above for the mentioned frameworks that are already adopted by specific banking, crypto, media, and other applications.
Moreover, InTheBox is accepting contract work to build targeted plugins for the application identified by the purchaser. The graph below shows the number of attack plugins offered per country in the “InTheBox” dark web store and illustrates their global impact.
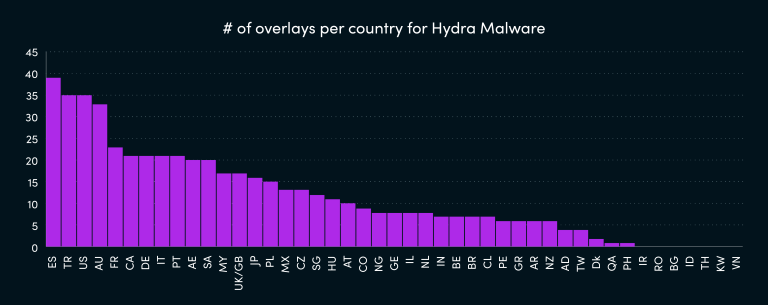
The danger of groups like inTheBox lies in their ability to provide a dramatically low entry level for implementing such customized attacks, since pricing is so inexpensive for one of these attack plugins. Once the plugins are injected, they use proven frameworks to transport the stolen data to Command and Control servers.
Enterprises turning to self-defending technologies to stop overlay attacks.
Why are overlay attacks so different than any other mobile threat? Because it’s a complex attack that takes advantage of a mobile app that isn’t properly monitored by its developer or its operator. And the needed intelligence to stop such attacks is available—it’s just not yet deployed by most developers at the onset of their deployment.
The “professionalism” surrounding mobile app-involved attacks is unprecedented in 2023, and the developer-deployed defenses need to be just as powerful as the threats they face. Otherwise, users will become disgruntled—and brands will become tarnished. Security as a differentiator will be key, especially given the not-so-distant hindsight that will undoubtedly rear its head.
Verimatrix XTD, with its zero-code yet vast monitoring and detection capabilities, was specifically designed to defeat these types of mobile app-focused attacks head-on with speed and accuracy. Verimatrix XTD arms developers with a comprehensive set of security features that include app shielding with continuous monitoring of the app ecosystems—sniffing out such attacks and allowing developers to protect their users via local countermeasures within the app as well as powerful server-side countermeasures.
In an overlay attack, the code of the legitimate application is not attacked or compromised. Therefore, hardening (preventing) the app alone will not help. This is where XTD’s additional services shine. Verimatrix XTD can detect when a malicious app takes over the protected app screen. XTD can also help with the first response to mitigate damage by giving, e.g., banks the needed real-time information to hold the transaction that is affected by overlay attacks.





Tool Sprawl Versus No Security Tools At All