Just a few months ago, the Computer Security Incident Response Team of the Polish financial sector (CSIRT KNF) issued a detailed analysis of HOOK, a relatively new mobile app malware largely targeting financial institutions in Poland that has now spread worldwide.
Operating as a high-end, comprehensive Malware-as-a-Service, this threat presented an opportunity for VMX Labs to outline why such attack methods can wreak havoc on mobile apps that lack professional-grade, in-app security.
The reason that HOOK malware is an excellent illustration of the need for in-app security lies in its vast arsenal of capabilities to thwart third-party protections. Not only does it find and even completely remove antivirus and endpoint protection on devices, but it also uses complex overlays and large numbers of attacks to ultimately get its foot in the door of well-known financial institutions, such as top banking brands.
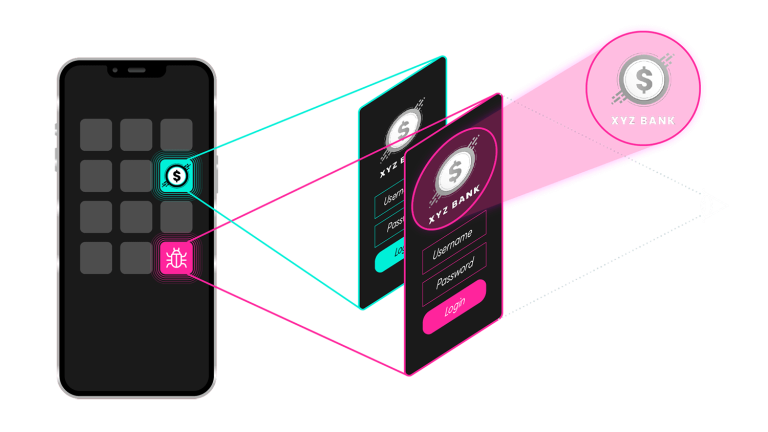
HOOK is a pre-prepared overlay that can be customized for 24 specific apps from Polish companies, including popular mobile banking, e-commerce, and utility apps. Hundreds more are available for companies outside of Poland, too.
HOOK is very dangerous; it can render anti-virus and endpoint protection useless. Additionally, it can prevent these types of security tools from being installed at any point during the attack, buying valuable time for the HOOK attack to meticulously seek out the apps it is targeting.
Traditional endpoint protection and anti-virus tools still serve as excellent lines of defense, even a necessary one. However, due to their standalone app design, they are inherently susceptible to attacks from these frameworks. As a result, an additional layer of defense becomes essential.
Sampling of attacks used by HOOK malware
Think of HOOK malware as a mobile banking trojan that uses hundreds of methodically-created launch overlays as its primary tool while harnessing a lot of accompanying attacks.
The overlay opens on top of the legitimate target mobile app and displays, for example, a login screen that looks just like the real one. The victim inputs a username and password, and HOOK’s key logging and key injection immediately steal the information. It also hides clicks and executes clicks for required actions.
Some of its attack tools include:
- Redirecting voice calls
- Accessing the local file system
- Controlling text messages
- Reading the GPS position
- Process control
- Software discovery & de-installation
- SIM configuration control
- Exploitation of firmware problems
- Additional malware downloads
- Reading, writing & sending WhatsApp messages
How HOOK malware functions
CSIRT KNF indicated that a part of these attacks exploited the mobile device’s accessibility service, an Android feature that enables disabled users to successfully use the device. HOOK exploits these services in order to obtain persistence and escalate permissions as needed by sending tabs, swipes, and keystrokes to the appropriate controls and putting overlays on top of the controls to hide the malicious activity, i.e., the malicious app requests new permissions and simply accepts them by clicking screen buttons through the service.
It also provides ways to intercept SMS as well as Google authenticators and has a reverse proxy so that sniff data can be abused and allow attackers to abuse these in real time. The ability to read, write, and send messages in WhatsApp is also quite notable, as it’s a new attack tool even for the HOOK developers themselves.
Clearly, once HOOK gets its hooves into the device, the only hurdle left is overcoming app defenses that contain protections within their code. It’s almost never worth an attacker’s time to attempt to break an app that is foundationally secure and monitors itself. The result? The only way HOOK could attempt to attack one of its targeted apps that happens to use in-app protection is to remove that targeted app. Thus, the attack is rendered pointless. The targeted app would no longer be available as a conduit for the crime. Why would one burn a bank to the ground if they were intending to rob it?
Now available for lease on the dark web for approximately $7,000 USD per month, HOOK’s makers see themselves as arming their “customers” with opportunities to steal extremely large sums of money. And clearly, many customers agree that the big initial expense is worth it because they know the majority of banking apps remain vulnerable.
What’s the appeal for criminals?
HOOK offers new exploits for the latest versions of Android. In other words, it’s really up-to-date compared to some cheaper alternatives that cost less than half or even one quarter of the cost. Additionally, there is a plethora of customization that either already exists via HOOK or is able to be easily offered alongside the standard MaaS “package.”
The large number of customized attack tools target very prominent organizations, greatly enlarging the pool of potential victims simply due to the sheer number of the organization’s mobile app downloads and users.
How HOOK malware can be contained
The complex and comprehensive attack approach, coupled with the widespread opportunity for victims, makes HOOK a form of malware to watch carefully. And Google is definitely watching, as the company announced this month the launch of its new Google Mobile Vulnerability Rewards Program (Mobile VRP). The new bug bounty initiative, which offers payments to researchers who identify flaws in specific Android apps, is another sign that in-app security is no longer a consideration but a critical element for safety. We applaud and support Google’s efforts.
As we stated previously, traditional security measures such as anti-virus tools and endpoint security are valuable and should not be discontinued, However, if you are a financial institution looking to prevent a HOOK attack, you should consider deploying additional cybersecurity countermeasures, both within the mobile app and on the external mobile attack surface.
Verimatrix XTD is one such solution, providing an affordable and user-friendly mobile app and mobile ecosystem protection. With its agentless, zero-code approach, it allows for easy and painless deployment, allowing banking customers to monitor a wider attack surface, including unmanaged consumer devices.
Verimatrix XTD effectively detects active attacks within the app and responds promptly, minimizing the potential for damage. It also monitors the perimeter of connected devices, analyzing data and predicting attacks. This enables organizations to proactively protect their mobile applications to guard against:
- Overlay Attacks
- Supply Chain Attacks
- Repackaging Attacks
- Payload Delivery Attacks
- Geo Spoofing Attacks
Armed with Verimatrix XTD’s comprehensive security offerings and expert support, security professionals in any industry can effectively mitigate the risks associated with mobile app vulnerabilities and secure their digital assets.




3 Security Imperatives for Vehicle App Manufacturers in 2024