VMX Labs has been studying ways in which cybercriminals are utilizing Android banking trojans to exploit Android accessibility services. In one case, it’s to ultimately use an automatic transfer system framework and PIX keys to easily steal users’ funds. The result can be an instant (and unauthorized) fund transfer out of a victim’s bank account.
The recent GoatRAT variant, as outlined by researchers at Cyble, is targeting Brazilian banks, but from a wider perspective, it shows that app developers need to implement greater protections that can sniff out this abuse on a mobile device. Where we see smoke today, there is likely to be a fire tomorrow.
Making the recent GoatRAT variant even more dangerous, it no longer needs to include some of the usual core banking trojan functionalities that we would usually expect to see during similar financial fraud. And, as Cyble pointed out, it looks as if the automated transfers seem to serve as the exclusive purpose of the attacks—not data or PII theft or anything else at all.
The trojan operates in a way that does not require it to seek or obtain standard permissions or authentication codes. As a result, organizations still need to nurture their existing, ever-advancing cybersecurity and authentication processes while also adhering to basic security practices that prevent trojans from infiltrating their systems, such as requiring biometric authentication to access mobile devices, avoiding clicking on unexpected links, and only downloading apps from the two trusted stores.
Many sources, such as Cyble, have indicated that GoatRAT started as a remote administration tool that was used to take control of devices, but now one of its latest versions clearly serves as the trojan described above, specifically targeting Brazilian banks, including NUBank, Banco Inter, and PagBank.
Hidden Activities: Screen Overlays & Accessibility Services
This new type of attack shows an unmistakable increase in the use of Android Accessibility Services, and this specific example uses those services to identify the intended target of the attack (verifying the correct target app is installed on the device itself) and then create screen overlays that are meant to conceal the activities of the attack occurring “beneath” it. Furthermore, all the needed user inputs are also conducted using Android Accessibility Services.
In the world of Android, Accessibility Services work behind the scenes to provide a helping hand to those who need it most. These services were born out of a desire to make technology more accessible for people with disabilities, with features like screen readers and speech-to-text that allow for seamless interaction with consumer devices. But the high level of administrative privilege for Accessibility Services can make them a prime target for hackers looking to exploit their capabilities for their own gain. Malicious actors can use Accessibility Services to perform a range of illicit actions.
What is a screen overlay attack?
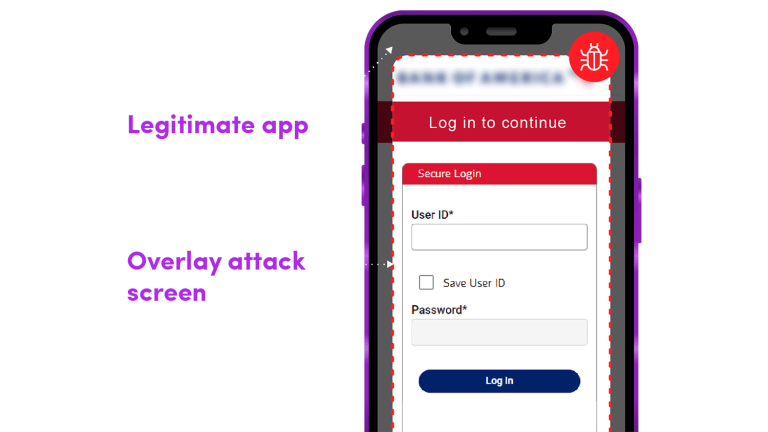
A screen overlay is a dangerous attack (commonly attacking Android accessibility features) that places an invisible window or screen on top of the running app to capture key entry without the user being aware this is happening. Hackers then trick users into sending information both to the legitimate app and to the bad guys.
For example, imagine you’re using a banking app on your phone. Suddenly, a screen overlay appears, prompting you to enter your login credentials. You assume it’s just part of the app’s normal interface and enter your information. But in reality, you’ve just handed over your sensitive data to a cybercriminal.
The potential harm of screen overlay attacks is clear: they can be used to steal personal information, financial data, and other sensitive information from unsuspecting users. In some cases, hackers have used screen overlays to install malware on devices, giving them access to even more data and control over the device.
How to prevent screen overlay attacks
So, what can enterprises do to protect their mobile apps from these types of attacks? First, they need to ensure that their apps are built with security in mind from the beginning. This means following best practices for secure coding, using encryption to protect data in transit and at rest, and regularly testing their apps for vulnerabilities. Integrating Verimatrix XTD Prevent into your CI/CD workflow is an example of shift left cybersecurity for mobile apps.
Second, companies should consider implementing security measures specifically designed to detect and prevent screen overlay attacks. This might include tools that monitor app activity in real-time, RASP, looking for suspicious behavior such as multiple apps running simultaneously or unexpected overlay windows appearing on screen. Again, Verimatrix XTD is an ideal solution for this.
Finally, companies should step up their mobile app monitoring game. Verimatrix delivers an amazing cybersecurity solution with Extended Threat Defense (XTD); allowing customers to prevent, detect, respond to, and predict threats to their mobile applications and the devices that connect to their critical infrastructure. This detection includes overlay attacks.
We have expanded our detection capabilities to the network, beyond application and device level detections. We can assess risk per application to protect the connection to the company’s critical infrastructure. All of this is now available.
For more information on Verimatrix XTD, a solution that more and more financial institutions are turning to to prevent this type of evolving attack, click here.





Tool Sprawl Versus No Security Tools At All