Mobile applications run within a sandbox. The sandbox is provided by the operating system (OS) and is intended to isolate each application, keepingthe code and data safe from prying eyes.
But what if the sandbox isn’t as secure as you think? Would that change your attitude when it comes to the security of your company’s apps?
A false sense of security
Verimatrix provides security solutions for some of the toughest industries, including Finance, Media and Entertainment, and Healthcare. From this unique view point, Verimatrix has been able to gather security data from awide range of mobile apps for a forthcoming security monitoring service.
Based on review and analysis of 75 million unique security events collected over the last 6 months*, it is clear that app developers cannot simply rely on operating system sandboxes for their app security. Putting too much trust in sandboxes can expose the apps running within them to excess risk.
Outdated operating systems
Security researchers regularly find vulnerabilities within Android and iOS. Google and Apple do a great job of quickly addresses these vulnerabilities and updating the operating systems – a process often known as “patching” – further hardening the sandboxes.
Actually, considering the complexity of a modern smartphone operating system, the number of vulnerabilities found is surprisingly low. A lot of credit goes to the developers and security teams at Apple and Google for that.
For a patch to be effective, it must be installed on the end user’s device.Though patches and updates are increasingly auto-installed, data still shows that 18.7% of devices are running an outdated OS version – which means that these are running with known vulnerabilities**.
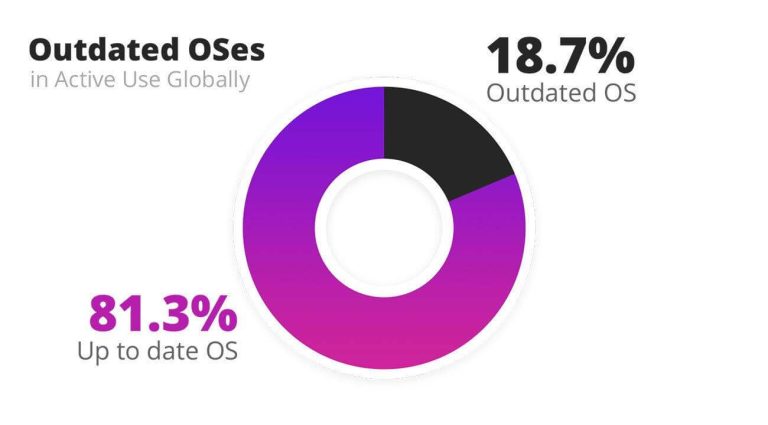
For those familiar with Apple’s aggressive rollout of new versions of its Operating Systems, it should come as no surprise that Android devices are3 times more likely to be running an outdated OS version.
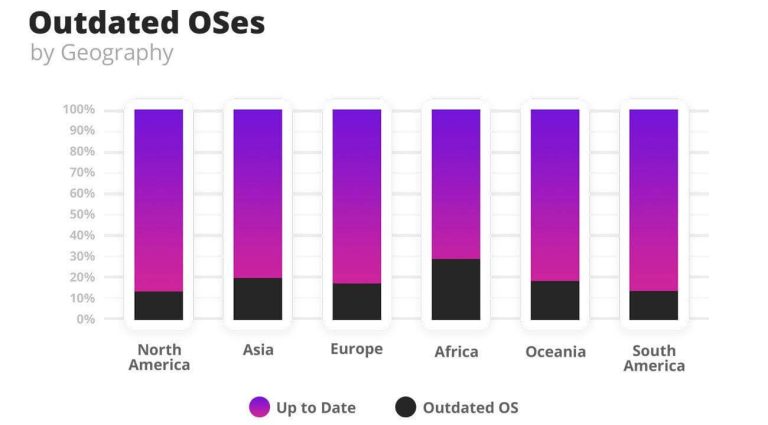
These rates are similar with little variation across the continents; though in Africa there is a slightly higher prevalence of older phones with older OS versions.
Rooted devices
“Rooting” a phone is the act of giving applications and/or the user increased privileges. In effect, this means removing the sandboxes the operating systems puts around applications.
Attackers use rooting as a means to better understand how an app executes (which is known as “dynamic analysis”) or to modify an app’s behaviour while it is running (e.g. to cheat a game).
Rooting is not always carried out for malicious intent; many users root their phones to simply get more control over their device (e.g. to change the look-and-feel of the operating system). When users root their phone, they increase the risk of malware attacking legitimate apps.
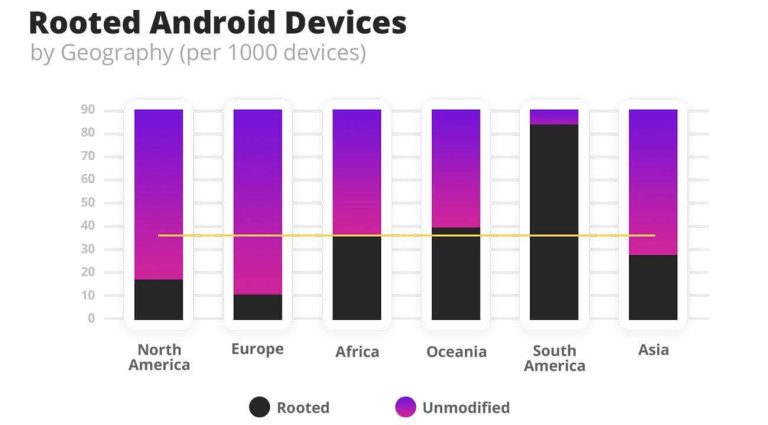
Verimatrix’s data shows that globally, 36 out of every 1000 Android devices are rooted.
On iOS, “jailbreaking” is the term used; but the effect is the same rooting. While it is possible to jailbreak even the latest iPhones, the phenomenon is less popular than rooting Android devices.
There is a wide variation in prevalence of rooting around the world. In Europe, it is as low as 10.7 per 1000 Android devices, whereas in South America it is 83.7 per 1000.
A world on fire
There was a substantial number Amazon Fire devices in the data set (which are excluded from the figures above).
Amazon’s Fire OS is based on Android.
Interestingly, rooting Amazon Fire devices is virtually non-existent with less than 1 per 1000 devices rooted. It’s not all good news though– 62% of Fire devices are running an Operating System based on Android 5, which was released in 2014.
Self-defending apps
At Verimatrix, we are fully aware how easy it is to lift an application off a phone, taking it out of its “secure” sandbox in preparation for reverse engineering. Even seasoned security professionals are often surprised when we demonstrate extracting and reverse engineering an app in a matter of minutes using freely available tools.
As such, we’ve long advocated the need for apps to protect themselves from reverse engineering using app hardening tools.
*5th March 2020 to 24th September 2020
**Outdated on iOS means OS version released before 24th September 2019; for Android it means running earlier than Android 8.





