There’s a consistent trend in the world of computing: moving from dedicated hardware to off-the-shelf components with software defined use cases. This trend is consistent in the world of security, which is moving from hardware guarded perimeters to intelligent software protection.
Verimatrix has been at the convergence point of these trends, and we have even been praised by Omdia for our agility and resolve in developing new, forward-thinking products. This is true across all industries we support, from content security with our VCAS products to our continued support of the evolution of payments security.
Innovation driven by convenience and fraud reduction
Innovation in payment technology is driven by two questions:
- How do we get more people to make payments on our platform? This means making it easier and more convenient to pay.
- How do we reduce fraud? By making payments more secure, cost is driven out of the system and consumer trust is increased (which, in turn, means that more people will make payments on a trustworthy, secure platform.)
Looking at this timeline of payment technology innovations, you can see that each new product or launch was driven by either convenience or fraud detection:
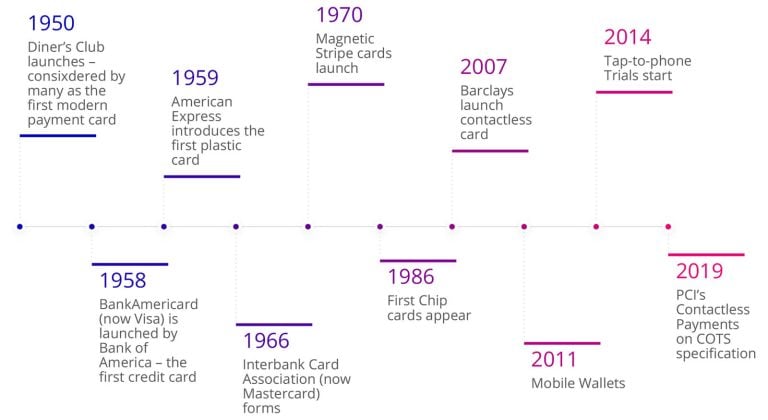
From chip to software: Paving the way for tap to phone transactions
When card-based mobile payments began, security leveraged the traditional “chip” card approach. Either the SIM card or a dedicated chip (aka a Secure Element) in the phone was used. This was a hardware security model. It was quickly realized that unless you control the whole ecosystem (á la Apple Pay) this model was very inconvenient to deploy.
The breakthrough came when Google opened up the NFC antenna on Android phones through an interface called Host Card Emulation. Suddenly, everything could be built in software – making it very easily to deploy fully featured card-based mobile wallets.
But what about security? This is where innovative solutions come in, like Verimatrix’s Software Shielding technology. The right security approaches deployed in software can protect mobile wallets at levels equivalent to hardware-backed solutions, but with none of the inconvenience.
Consumer off the shelf (COTS) devices
The success of ground-breaking companies like Square and iZettle proved that there was a demand for more accessible payment acceptance. Suddenly, merchants who would never have been able to consider dedicated Point of Sale (POS) terminals had an affordable and convenient way to accept card payments through new mPOS solutions.
These early mPOS solutions used a hybrid approach—coupling off-the-shelf mobile phones for the user interface and connectivity, while utilizing dedicated hardware to perform the transaction against the card and meet security requirements.
It was only a matter of time before acceptance made the same transition as issuance: moving to pure software POS terminals (SoftPOS) running on COTS devices. The only real hindrance was the need to “honor all cards” including those with a chip or magstripe. The increase in contactless payment usage removes this blockage – an Android phone with NFC can easily talk with a contactless card or phone the same way that a dedicated POS terminal can.
Secure Tap to Phone Payments
Early tap to phone trials started in 2015 and the approach was officially approved in 2019 with the launch of PCI’s Contactless Payments on COTS specification. This has accelerated the number of solutions in development.
PCI is an organization focused on payment security, so it’s not surprising that the recent specification defines strict measures that must be implemented. As a security-focused organization, PCI will never compromise on security just to aid a more convenient deployment model.
Modern in-store card payments are based around a cryptographic challenge-response. The terminal generates the challenge, which the card then signs to authorize the transaction. Keeping that cryptographic operation secure is the aim of the PCI specification. If this operation is safe, then the payment transaction is secure.
An important step when launching a new Tap to Phone implementation is the required audit by an approved security lab. These labs conduct an independent assessment to ensure compliance with the PCI specification. For consumers, compliance means that they can continue to trust payment networks. For vendors, compliance should be viewed as more than an entry requirement, its real aim is to minimize exposure to risk for them and all other stakeholders.
Protecting transactions on COTS devices with app shielding solutions
Operating on COTS devices means that the cryptography must be performed in a pure software environment – which requires whitebox cryptography and wider app shielding technologies. Without this hardening, the SoftPOS application will be vulnerable to attack and payment processing will be exposed.
Verimatrix has brought this expertise to banks building issuers wallets over the last 8 years; and the company now brings these solutions to technology vendors, Point of Sale manufacturers, and payment processors who are making the switch to SoftPOS.
If you are embarking on this path or starting to engage with a security lab, then contact us to discuss how Verimatrix can help smooth your process.





