Protecting your code is the key to protecting yourself from intellectual property theft. Of course, it’s also useful for protecting it against general cybersecurity threats. Fortunately, there are low-cost options that make it hard for malicious actors to detect weaknesses. The topic of this guide is code obfuscation and how you can use it.
“Obfuscation” describes any process of intentionally making something difficult to understand. Similarly, code obfuscation is the practice of creating code that is difficult for people and computers to understand.
Regardless of the chosen technique, obfuscation serves the same purpose in any given case. Also, all code obfuscation techniques offer similar protections. However, techniques vary in terms of:
- Difficulty of implementation
- Efficacy in preventing cybercrimes
These are just the defensive applications of code obfuscation. Unfortunately, the bad guys often obfuscate code for their own purposes, too.
Reasons for code obfuscation
Let’s start with the good, then go over the bad and the ugly.
Defensive code obfuscation
Code obfuscation techniques are practiced as a cybersecurity measure in order to protect against:
- Reverse-engineering attempts
- Intellectual property theft
- Trade secrets theft
- Data breaches and identity theft
- Piracy
- Discoveries of vulnerabilities (vulnerability exposure)
- Tampering
- License or permissions abuses
In all these cases, code obfuscation is a legitimate measure against malicious actors. It protects the integrity of the organization’s code and prevents common abuses against vulnerabilities found in code.
Code obfuscation is one key measure for protecting sensitive algorithms and proprietary methods. But it is also used by many companies to prevent software piracy. It’s also used as a protection against unauthorized modifications.
Malicious code obfuscation
Cybercriminals can also benefit from code obfuscation techniques. They use obfuscation to hide their malicious actions and make them appear benign.
One common example of criminal obfuscation techniques is malware concealment. Code obfuscation can enable people to conceal malicious code under the cover of legitimate software or files. Similarly simple and common methods include obfuscating malicious URLs, HTML, or JavaScript code. These techniques can make their attacks harder to detect until it’s too late.
Common code obfuscation techniques
There are several methods for code obfuscation. All these approaches make code harder for both humans and computers to comprehend, ultimately making it challenging, if not impossible, to reverse-engineer the code.
1. Encryption
One common way to obfuscate code is to encrypt some or all of a program’s code. Code encryption, as an obfuscation technique, means encrypting some portion of a codebase to protect its contents from prying eyes.
Encrypted code is then decrypted during runtime. Or, it is dynamically loaded into memory during execution, which adds more security. Often, the encryption of sensitive strings is underdone. Many organizations don’t find it necessary to heavily encrypt entire codebases.
2. Metadata and unused code obfuscation
Another common and simple option is to remove potentially risky metadata. In this technique, the metadata is then replaced with meaningless class and variable names. Lastly, meaningless and useless code is added to the script. Renaming variables is a relatively powerful and simple step that can often make a big difference.
By combining these three steps, you are throwing off any malicious actor or software trying to understand your code.
This is often done in a different and automatic way by tools appropriately titled “obfuscators.” Of course, it can also be done manually, but this can lead to unintentional difficulties within your own organization if not done carefully and methodically.
3. Simple restructuring
Code restructuring occurs when someone modifies the structure and flow of code without affecting its functionality. It’s a simpler alternative to the previous method.
Examples include:
- Changing the order of statements in a way that doesn’t affect functionality
- Adding unnecessary loops or conditionals
- Creating strange and convoluted nested structures, which, again, don’t affect functionality
4. Inserting dead code
You can also just insert dead code into the codebase. The only purpose of this code is to confuse malicious actors attempting to analyze your code. This technique is also referred to as “dummy code obfuscation.”
Key benefits of code obfuscation
There are both benefits and drawbacks to code obfuscation. In general, the benefits will outweigh the limitations. But understanding the limitations is key to avoiding the drawbacks and ensuring robust protection.
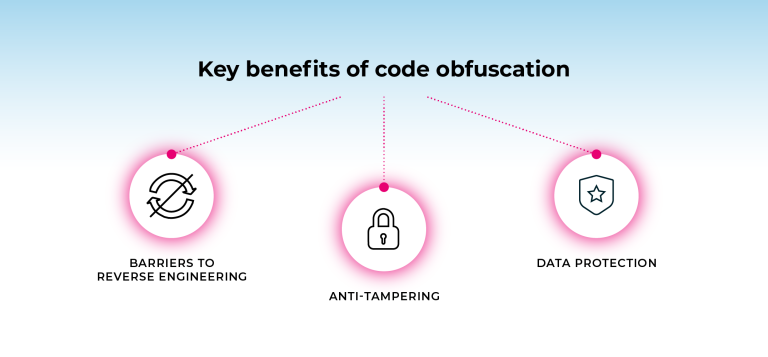
Barriers to reverse-engineering
Reverse-engineering occurs when attackers try to analyze a piece of code and understand its functionality. They scour through it manually or with the aid of software and look for:
- Weaknesses
- An understanding of its workings
- The functionality and how it can be replicated
Obfuscating your code makes their job much harder. Their attempts at reverse-engineering the code will be frustrated by their lack of understanding of what they’re looking at. The logic of the code will be at least partially lost on them, and the functionality will be harder to replicate.
This is important to remember when you are trying to protect your trade secrets and intellectual property.
Anti-tampering
Attackers trying to modify your code for malicious purposes will be similarly confused. If they are trying to modify certain functionalities without damaging the code’s overall functionality and integrity, they will have to dig through a maze.
This benefit is why code obfuscation is an important part of security. It makes it harder to take advantage of vulnerabilities in your:
- Authorizations
- Permissions
- Licensing
- Other key areas
Tampering with these key areas in a way that would benefit an attacker requires an understanding of the codebase they are dealing with. So, obfuscation isn’t just a cybersecurity booster; it’s a key component of trustworthy software.
Data protection
Perhaps an even simpler concern is a data breach. The way obfuscation protects your data is equally simple. If attackers gain access to your code, it will be very challenging for them to make any sense of it.
This is why, when you’re engaging in code obfuscation, it’s important to focus on sensitive data. Using the techniques we discussed above, you can protect your important data from attackers looking to commit identity theft or financial fraud.
Limitations of code obfuscation
Understanding these limitations helps you avoid shooting yourself in the foot when obfuscating your code for defensive purposes.
Increased complexity
Code obfuscation, by definition, complicates your codebase. While this makes it harder for malicious actors to cause harm, it also makes it harder for your own organization to operate.
This means that code obfuscation may:
- Make your code harder for employees to understand and develop
- Complicate debugging
- Introduce new errors or bugs
- Hinder internal collaboration
- Make onboarding trustworthy new employees or contractors more difficult
These problems can be addressed by one of two courses of action:
- Systematize your code obfuscation processes in an internally coherent way that smooths internal SOPs
- Use security frameworks that effectively obfuscate your code while making it seamless to work with
In any case, weigh the difficulties your code obfuscation efforts will cause against the security benefits they will produce. Ask yourself how each action you take will affect this balance.
Potential performance degradation
Many code obfuscation techniques necessitate additional processes when running code, which can slow down performance. For example, string encryption can slow your software’s performance.
The main drawback here is that your execution times may slow down. Again, this requires you to engage in a balancing act that weighs security benefits against drawbacks. In this case, you must balance increased security against lower performance.
Code obfuscation is not 100% impenetrable
Code obfuscation is not foolproof. There are several ways attackers can attempt to work around it. Even at its best, code obfuscation is still not a strong standalone defense.
With time, skill, and additional resources, attackers may be able to reverse-engineer obfuscated code. They need to work out the logic of your obfuscation techniques wherever possible. They may also need to decrypt code in some cases. These are difficult tasks, but they are often far from impossible.
The way to work around this challenge is to:
- Use complex but well-designed obfuscation techniques that are
- Hard to work around from the outside
- Easy to continue working with from the inside
Use obfuscation alongside other defensive measures like secure coding best practices, secure architecture, and security frameworks
Risk of self-sabotage
Self-sabotage is always possible with code obfuscation. Every one of the above drawbacks has touched on a potential negative that can result from the process.
Be careful to avoid:
- Introducing new errors or bugs
- Changing behaviors
- Undermining functionalities
- Making the codebase too convoluted for your own developers to work with
- Harming performance and frustrating legitimate end-users
The way to avoid self-sabotage and other drawbacks is to observe best practices when obfuscating your code.
Best practices for effective code obfuscation
Keep these practices in mind when engaging in code obfuscation to ensure the best possible results.
1. Balance
Balance is the most consistent theme in successful code obfuscation defense. A lack of balance can jeopardize maintainability, security, and performance.
The balance is not only between security and performance. It’s also between the security benefits you produce and the cost of labor that those benefits require. Cost-benefit analyses should be undertaken regularly and with every proposed change.
2. Testing and debugging
Testing and debugging are the other constant parts of effective code obfuscation. With regular testing and debugging, there are fewer opportunities for mistakes. There is also less risk to your code’s functionality. So, applications that are protected with code obfuscation techniques must be constantly monitored, tested, and fixed.
3. Updates
The efficacy of code obfuscation techniques is constantly shifting as cybercriminals develop new techniques of their own. Changes in the cybersecurity environment necessitate:
- Regular updates to your obfuscation techniques and countermeasures
- Updates and patches to any software solutions you employ for obfuscation and general security purposes
Staff members responsible for code obfuscation must be aware of new and evolving threats, particularly code injection attacks. Reading newsletters and following cybersecurity journals may spur action at a time when it is needed most.
Code obfuscation tools and frameworks
Many cybersecurity companies offer code obfuscation functionality through tools and frameworks. But there are also standalone code obfuscation solutions, such as Cyphor, a dedicated SaaS obfuscation platform.
In general, plenty of research should be conducted before using tools and frameworks. They all vary in terms of their efficacy in relation to your organization’s needs.
Here are a few key features that obfuscation tools and frameworks have in common.
- Renaming: They are given new names to hide their intended purpose. Built-in renaming features attribute new names to the key areas of functions, variables, and classes.
- String encryption: Most tools have this feature. It serves to encrypt sensitive strings in code, including APIs and URLs.
- Code shrinking: This is done to reduce the overall file size of obfuscated code.
- Control flow obfuscation: This simple but crucial feature rearranges the structure of code. This keeps the functionality roughly the same but makes it harder to read and understand your code.
The bottom line
Code obfuscation is a powerful tool for defense and offense alike. Any organization wishing to protect its code integrity should look into efficient techniques for code obfuscation.
It’s a necessary part of protecting intellectual property and protecting you from piracy and similar threats to income streams.
There are several techniques to be employed, but each has some drawbacks and limitations you must pay attention to. Lackluster code obfuscation can cause harm to a codebase while protecting it from outside threats.
The most comprehensive approach to code obfuscation is through obfuscation tools and frameworks. They contain the features you need to mystify your code in the eyes of any attacker. Look for the solution that fits your needs to avoid losing sensitive data that could have easily been shielded.